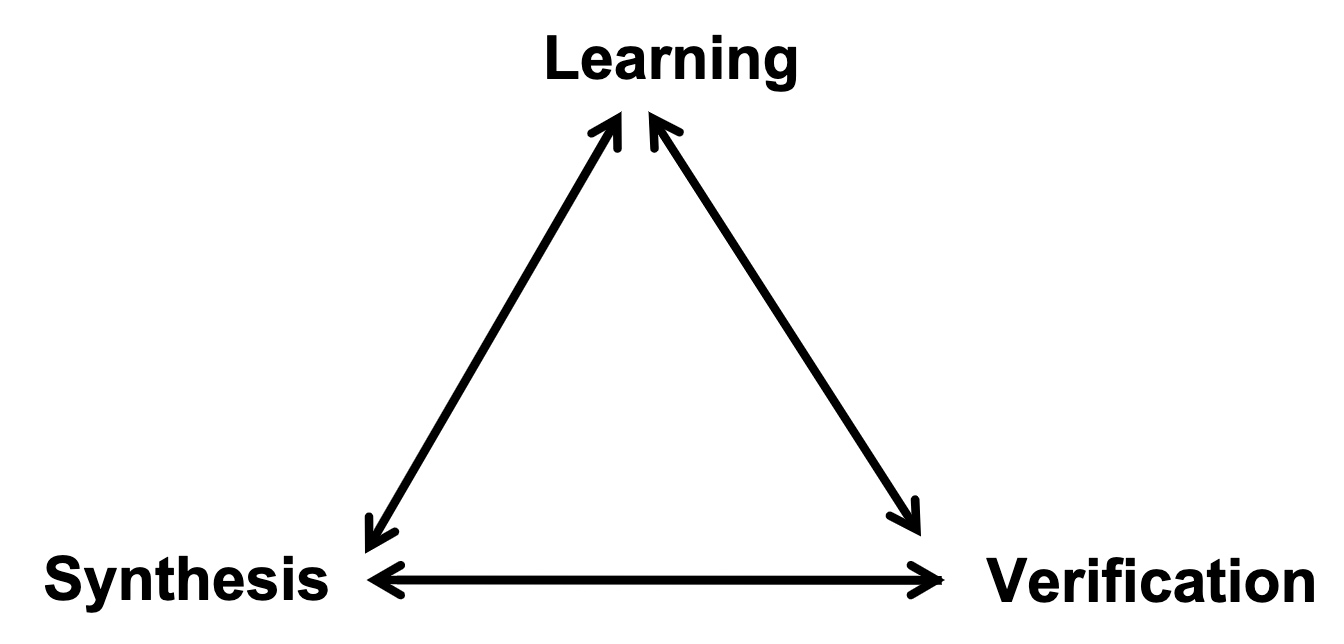
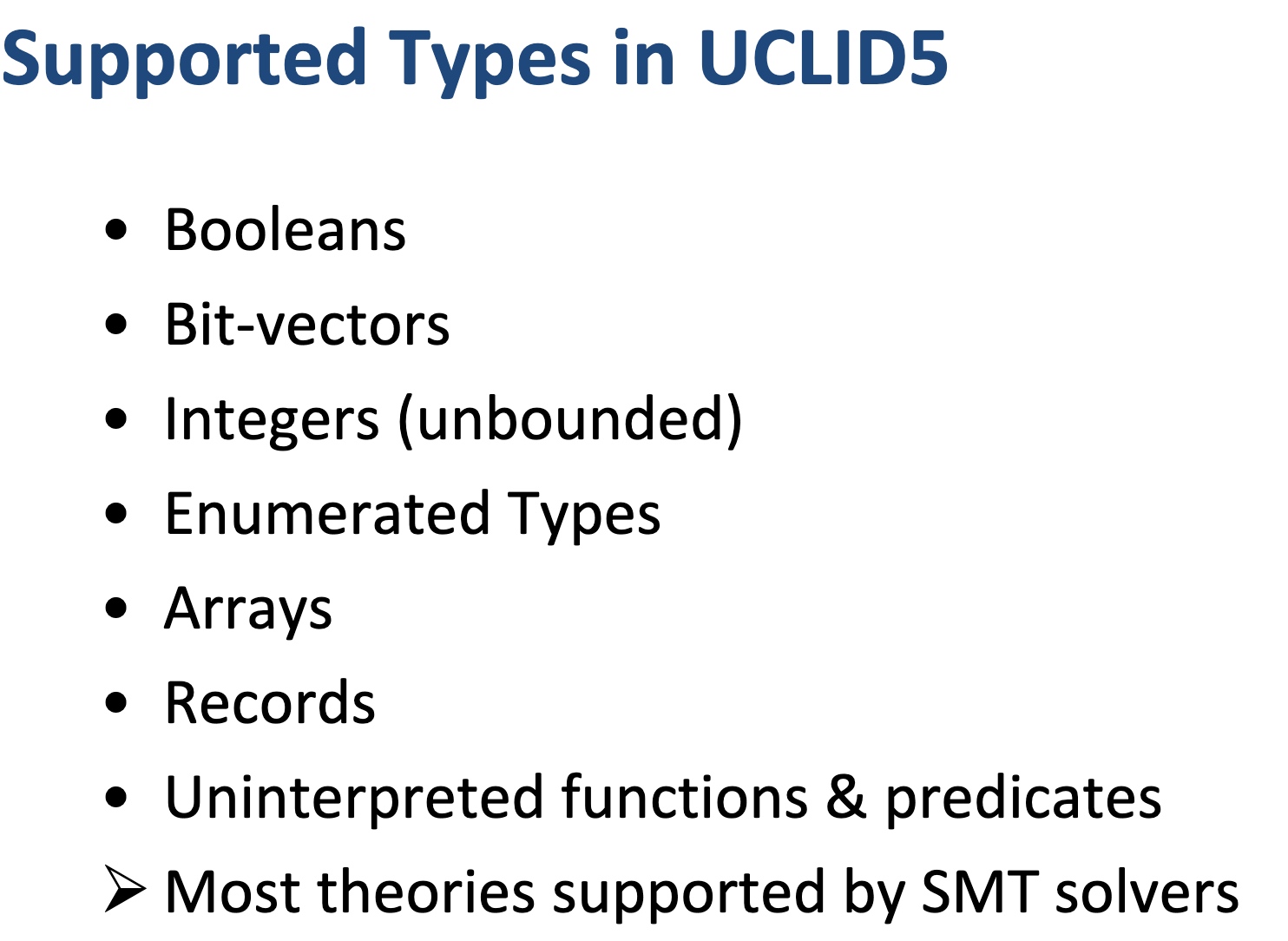
UCLID5: Integrating Modeling, Verification, Synthesis, and Learning
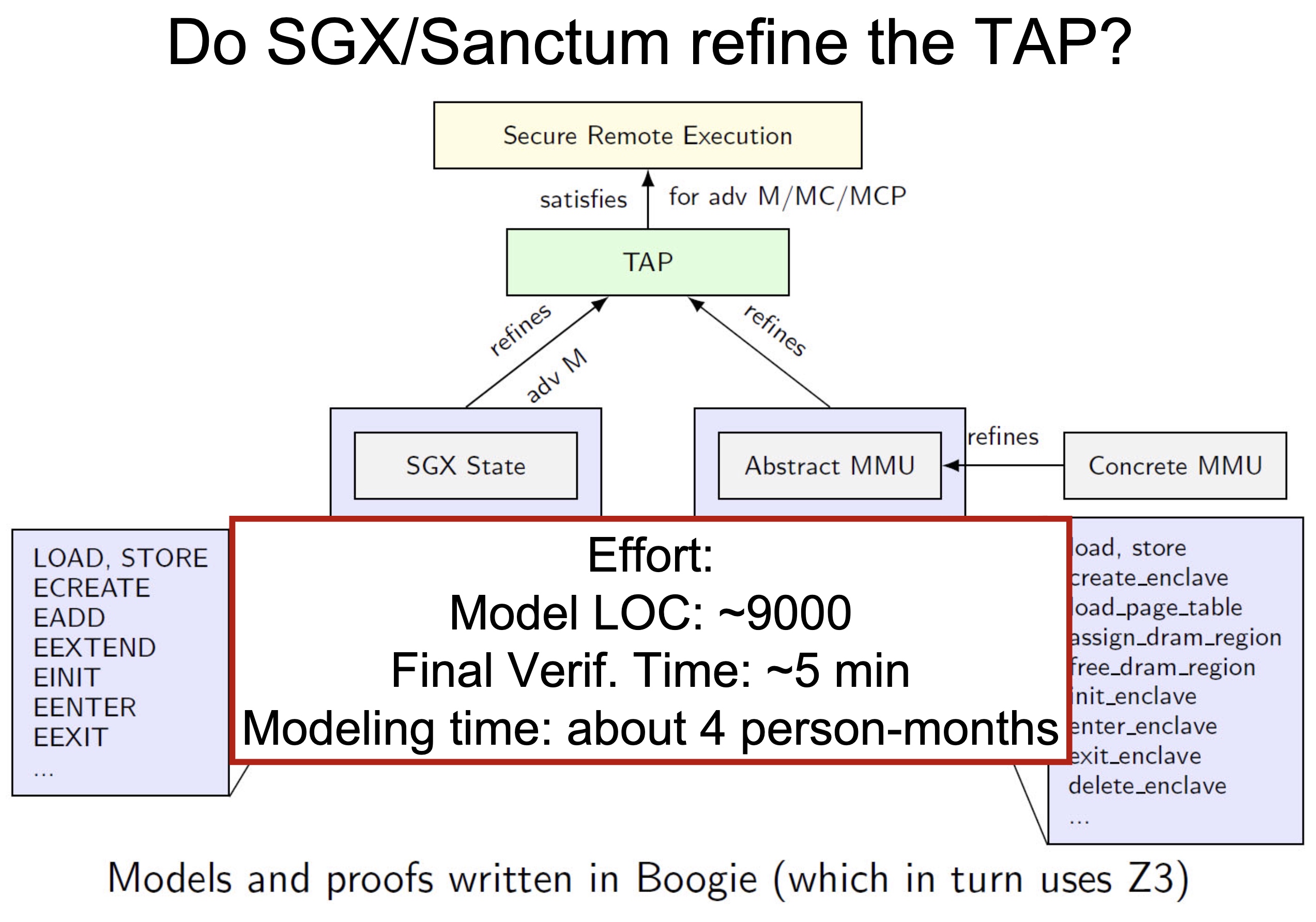
When I was browsing keystones‘ paper, they are applying a verification model called UCLID5, a new software toolkit based on z3 written in scala for the formal modeling, specification, verification, and synthesis of computational systems. The augmented efforts are merely making architectural implementations like NAPOT/S mode world change/exceptions in pmp reg mapping policy to Hoare logic and do the verification. To a greater extent, the Y86-64 introduced in CSAPP is verified by UCLID5, too.

The Goals
- Enabling modular modeling of finite and infinite-state transition systems across a range of concurrency models and background logical theories.
- Performing a highly-automated, compositional verification of a diverse class of specifications, including pre/post conditions, assertions, invariant, LTL, refinement and hyperproperties
- Integrating modeling and verification with algorithmic synthesis and learning.
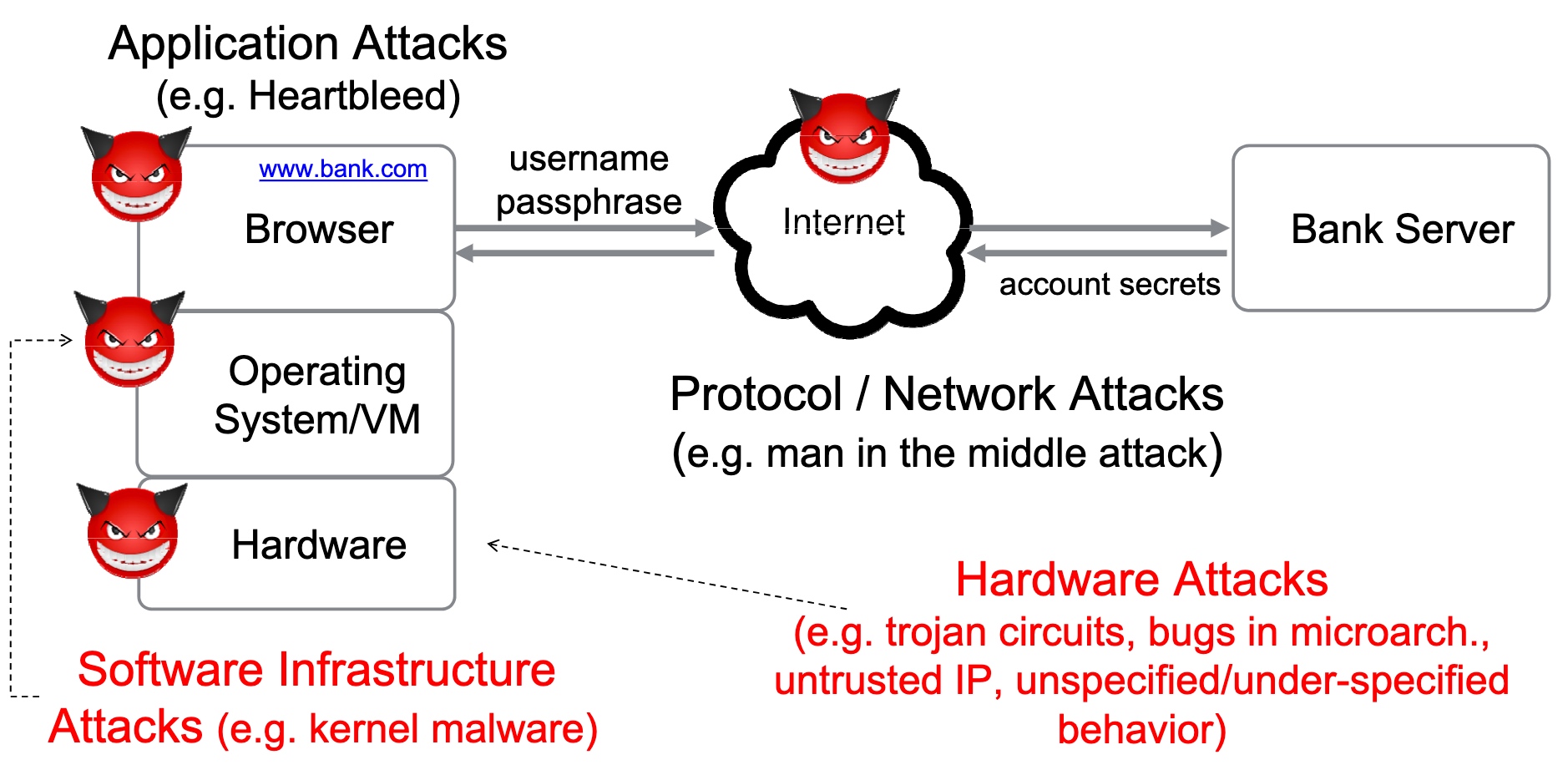
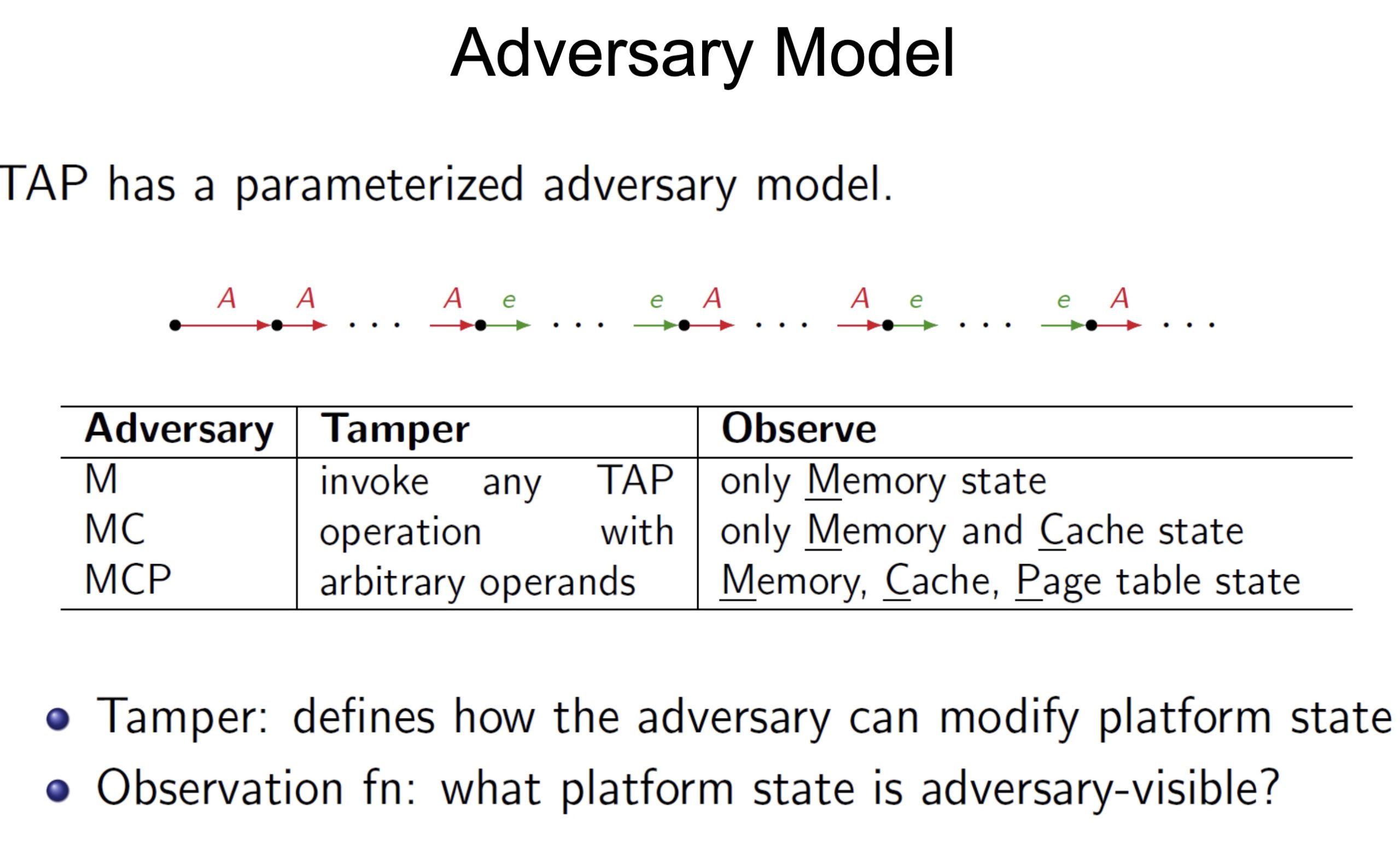
threat models
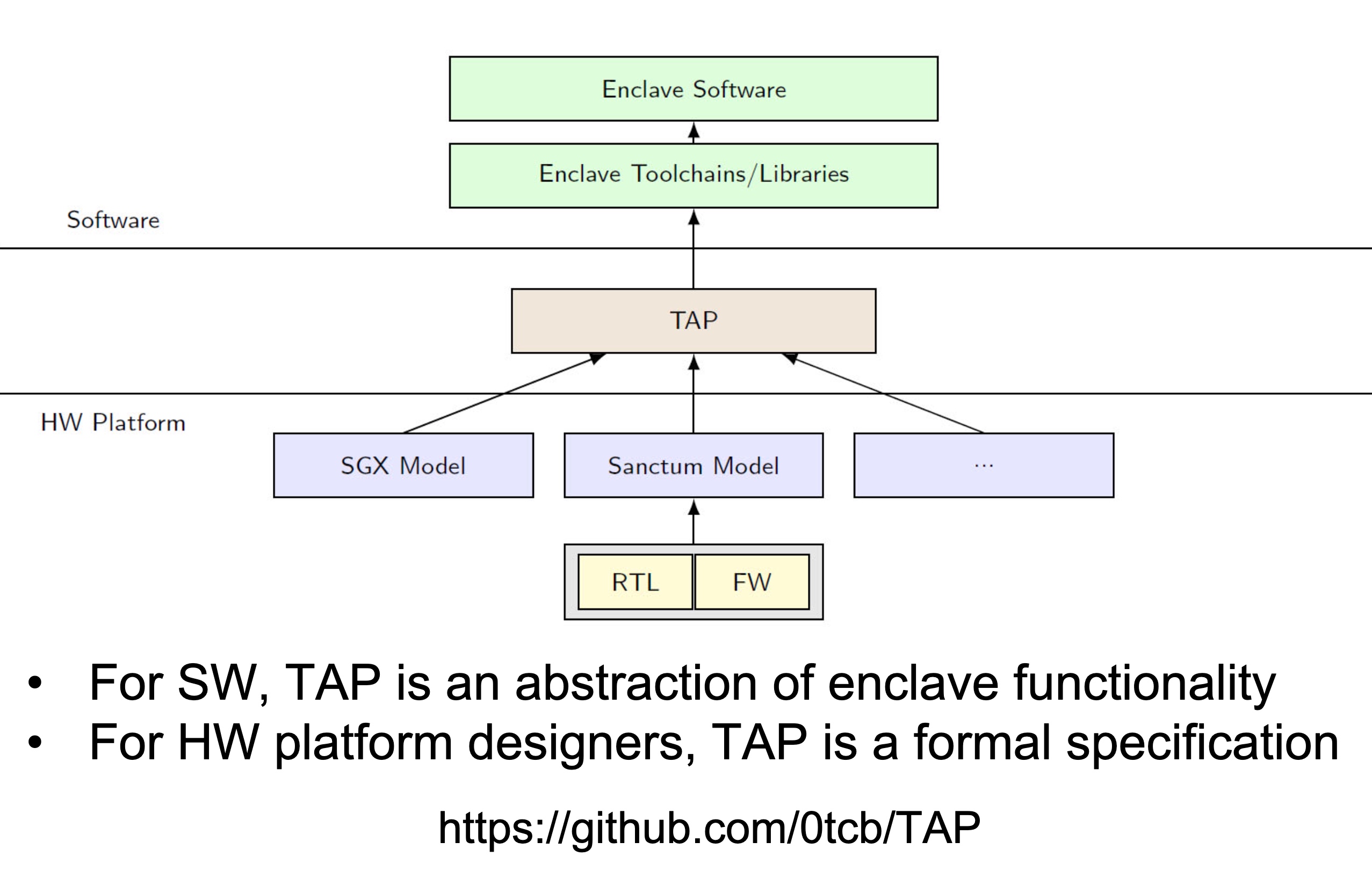
SRE
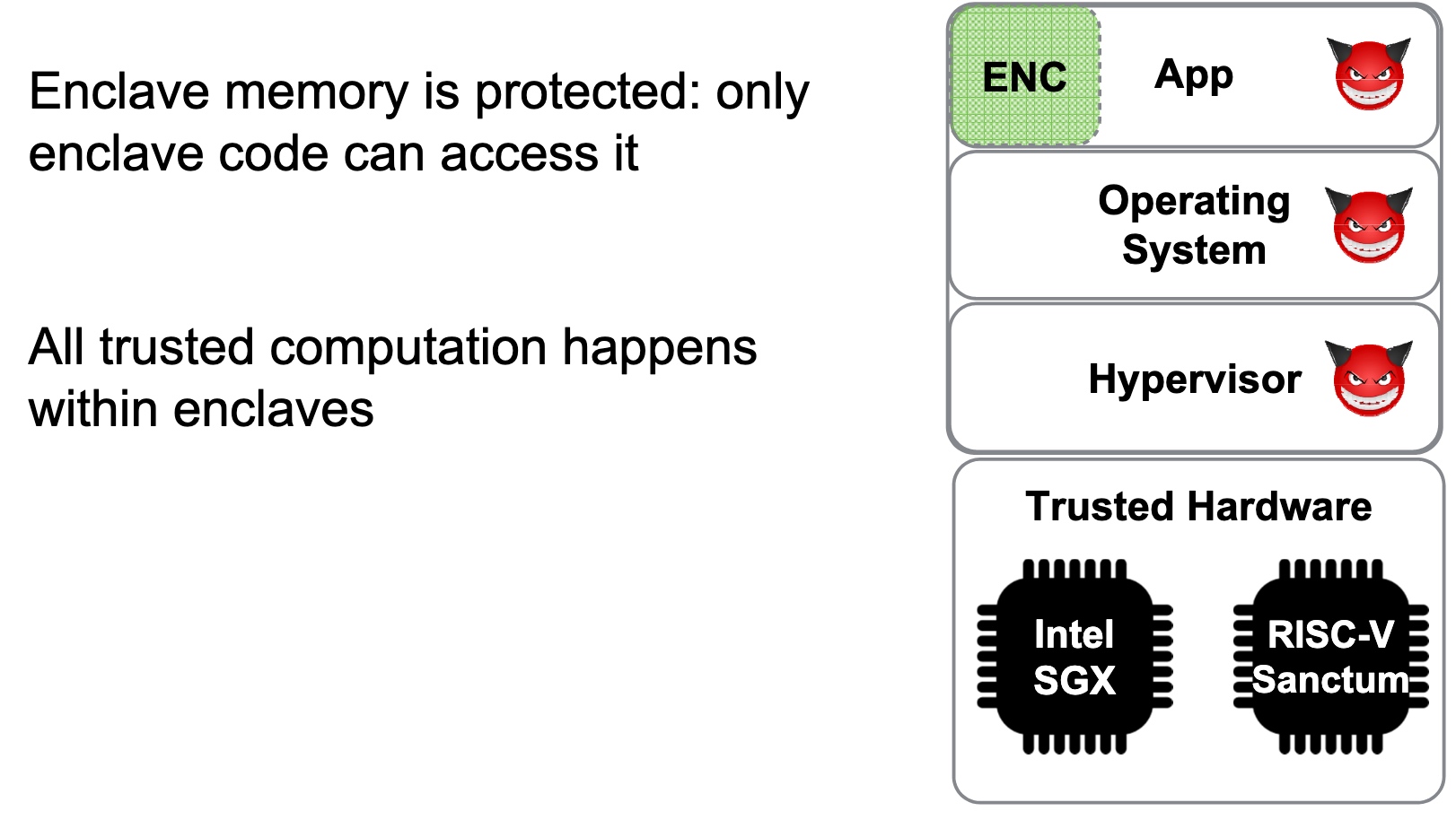
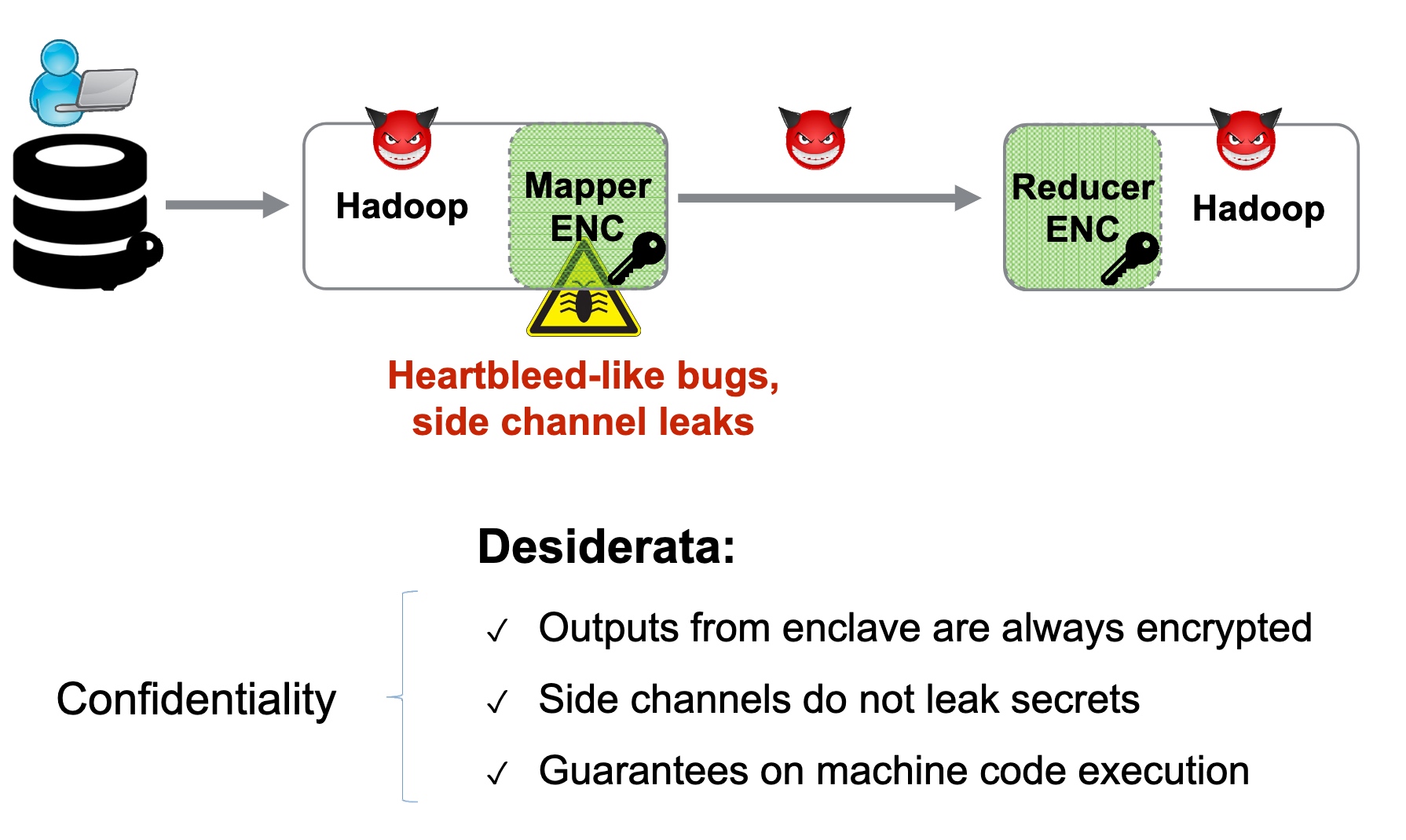
Heartbleed-like attack, side channels, and Meltdown/Spectre are also cast a lot on SGX/TEE. Stuff like secure remote extensions using trusted platforms is introduced. They formalized the enclave platform and made remote execution trustworthy.
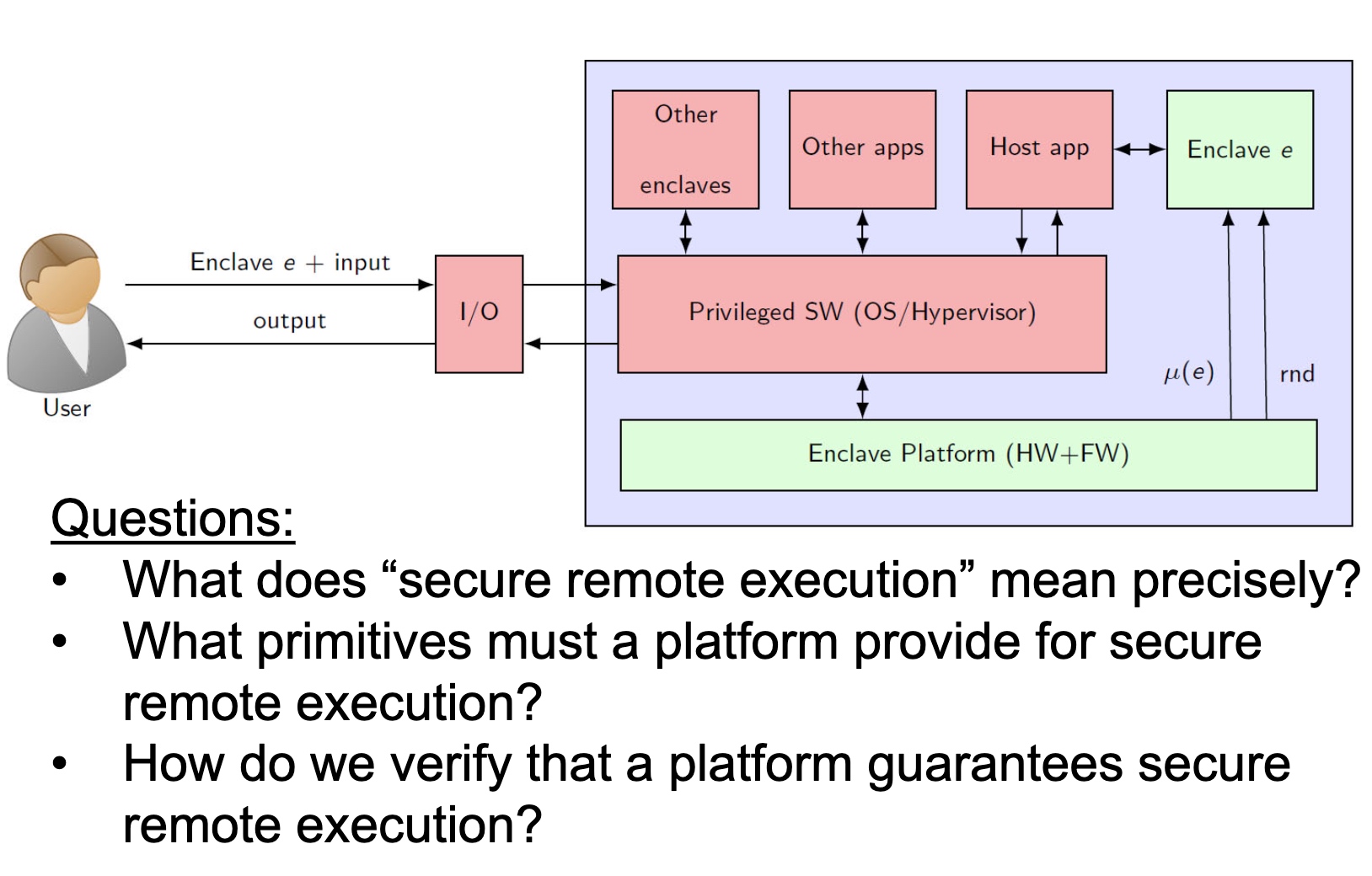
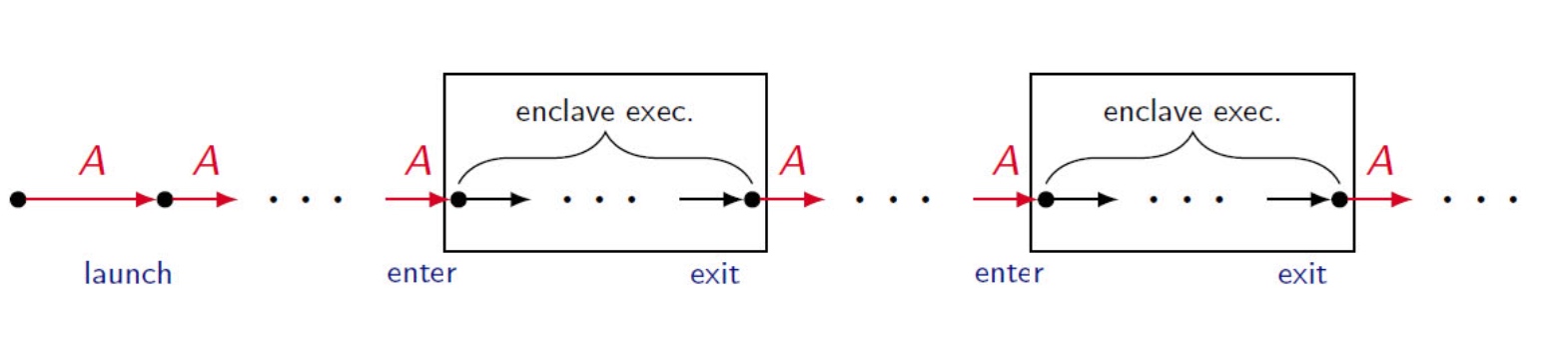
embodying enclave and adversary


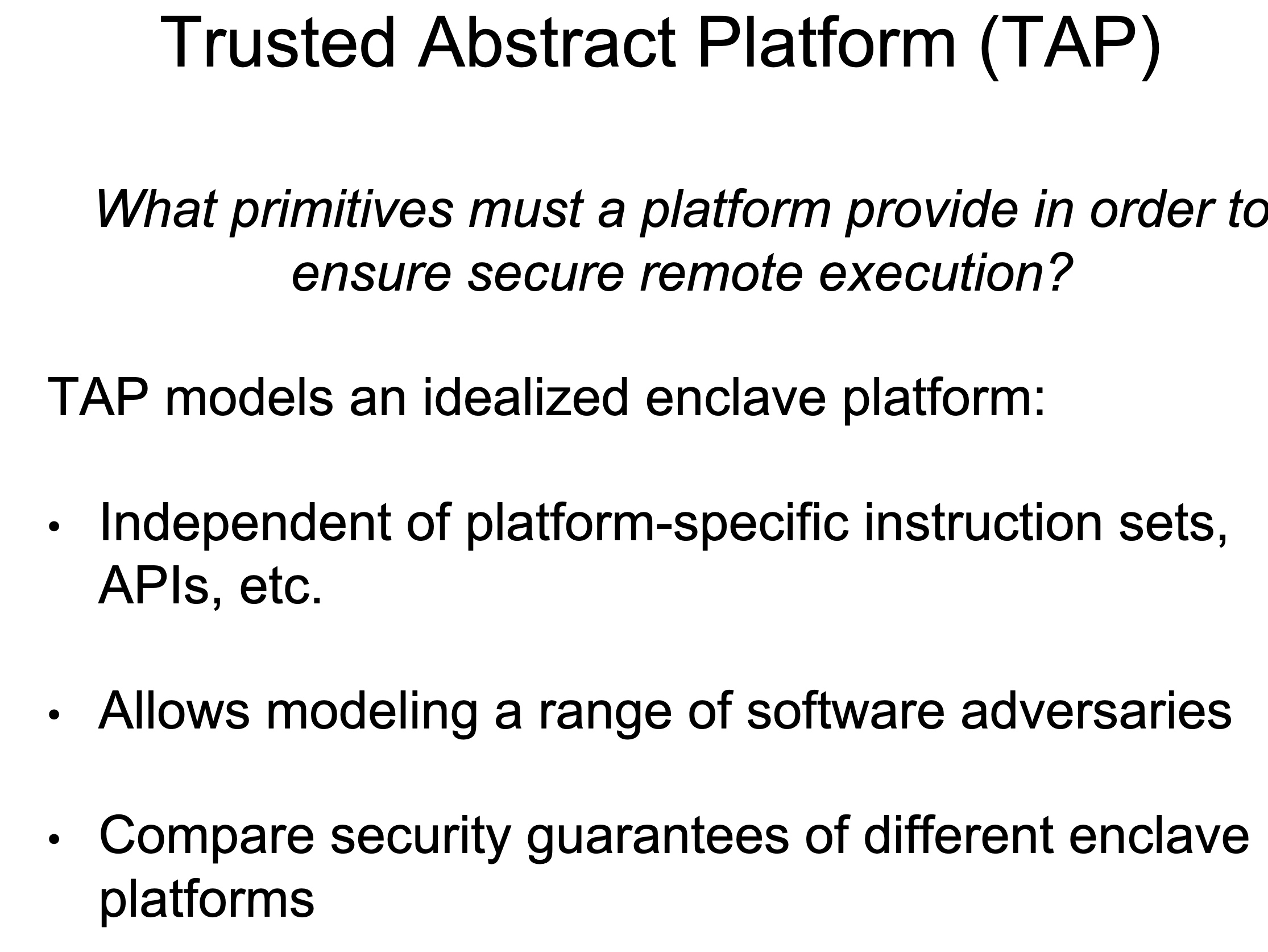
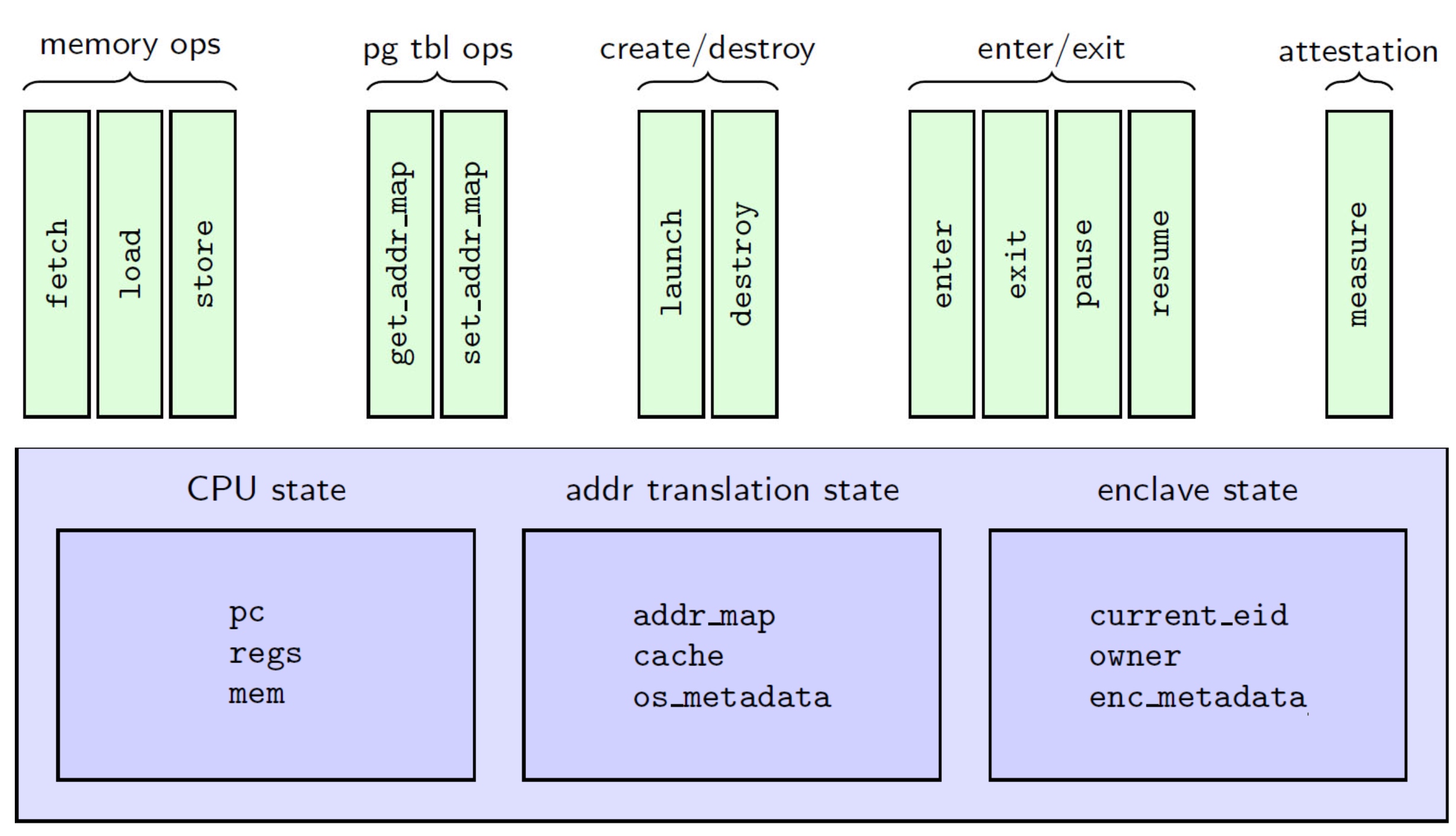

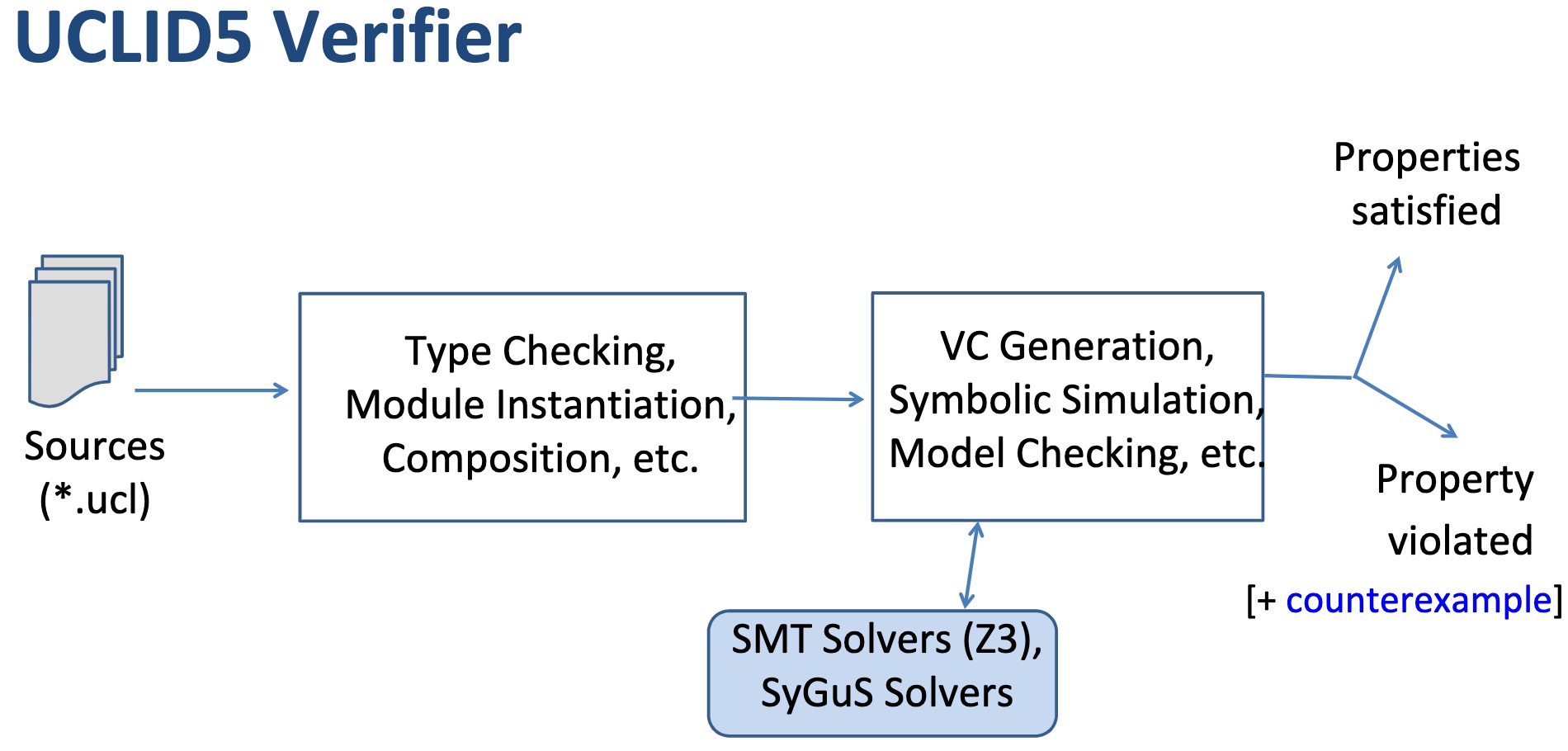
UCLID5 verifier
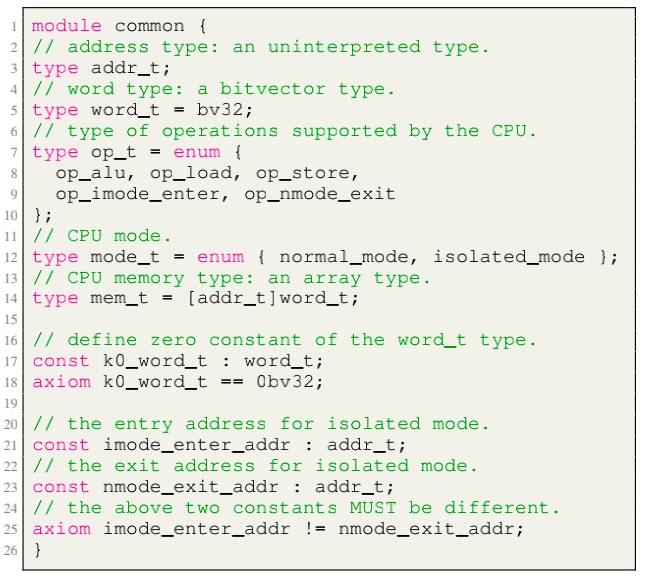
Modules, like LLVM, serve as the unit of re-use when declaring commonly used types, symbolic constants, and uninterpreted functions. The module uses uninterpreted functions to model instruction decoding (inst2op, inst2reg0 etc.) and instruction execution (aluOp and nextPC). Further, the register file index type (regindex_t) and the address type (addr_t) are both uninterpreted types. This abstraction is sufficient to model all kinds of CPU implementation.
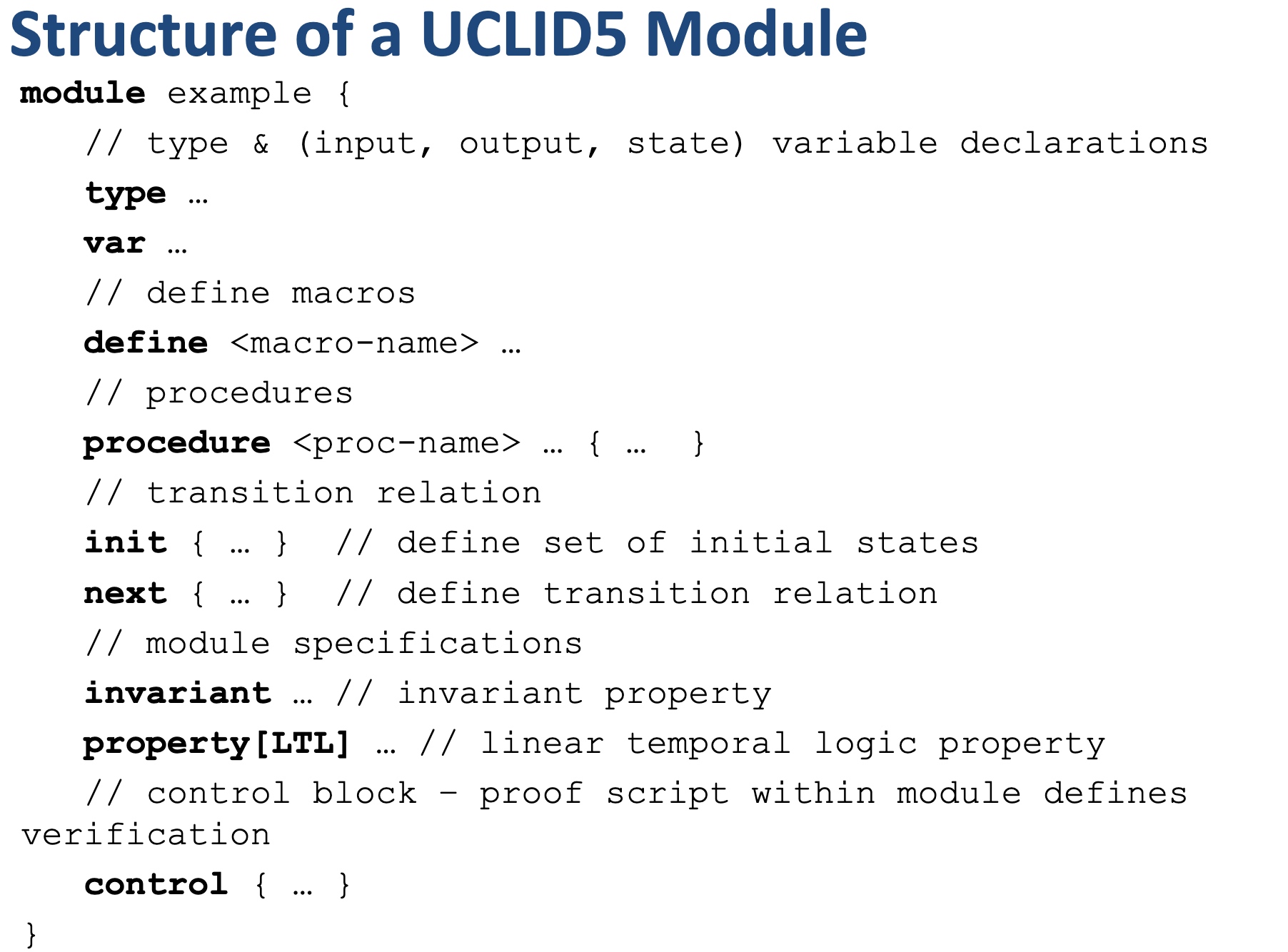
Structure of the CPU Model:
- Module common: serves as top-level type definition.
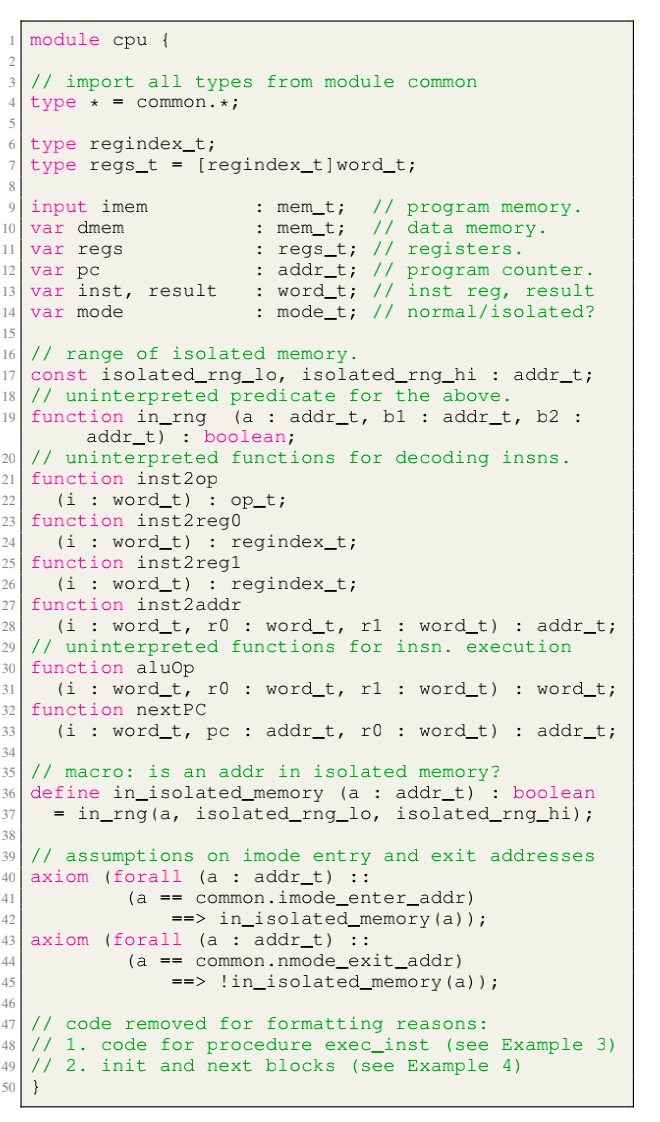
- Module cpu: defining the initial sate like reg/pc/imem/dmem, types are mode_t(isolated/normal) word_t addr_t(a range of addresses between
isolated_rng_loandisolated_rng_hi) init/next/exec_inst defines the transition system.
- Module main: the environmental assumptions for the verification and contains a proof script that proves, via induction, a 2-safety integrity property for the CPU module.
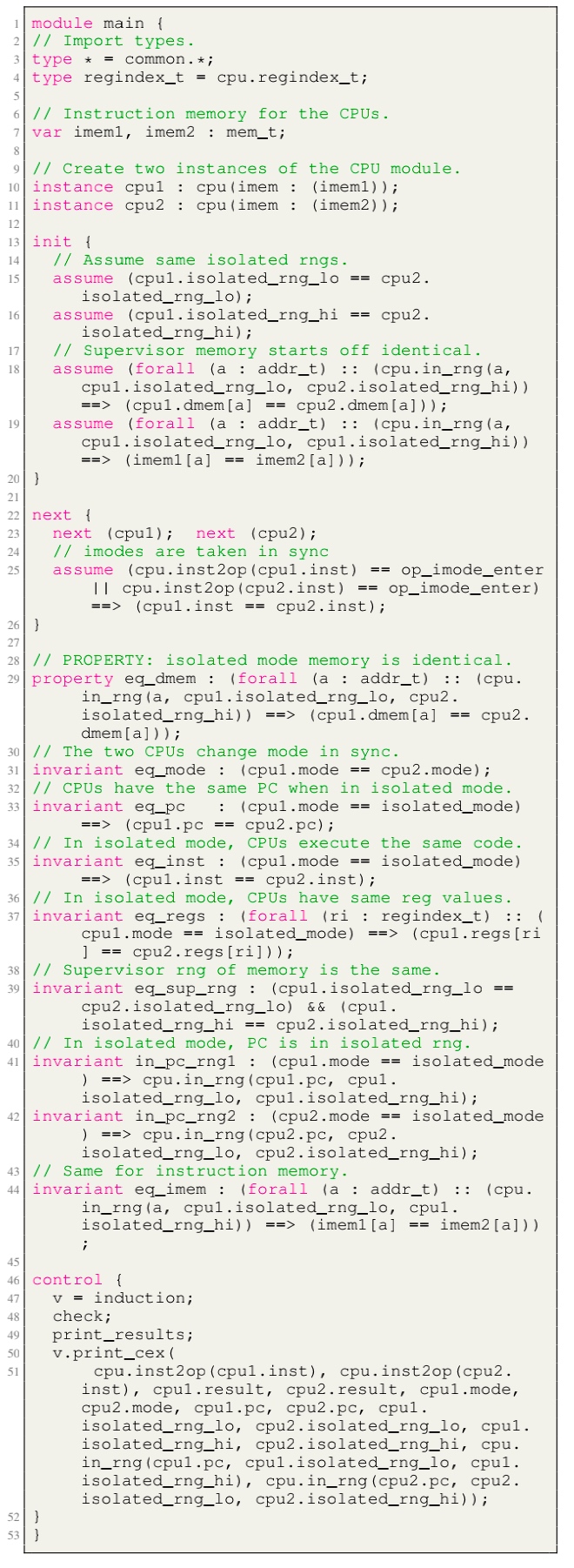
Other features
- Term-Level Abstraction: In term-level abstraction, concrete functions or functional blocks are replaced by uninterpreted functions or partially-interpreted functions. Concrete low-level data types such as Booleans, bit-vectors, and finite-precision integers are abstracted away by uninterpreted symbols or more abstract data types (such as the unbounded integers).
- Blending Sequential and Concurrent System Modeling:
- Diversity in Specification
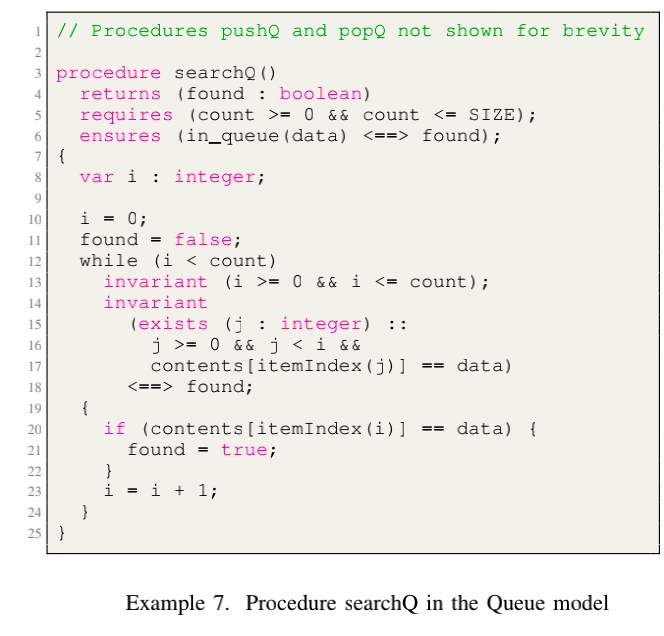
- Procedure specifications.
- Invariant
- while
- assume
- assert
- LTL
- Hyperproperties(k-safety): composing k copies of the system together and specifying a safety property on the resulting composition
- Procedure specifications.
- Modularity in Modeling and Specification
- Counterexample Generation
- Modular Proof Scripting
More for extended reading
Jeb android anti-compile tool on MacOS
Just Download here on Google.
And you may meet the problem just as me
yiweiyang ~ Downloads > JEB.android.decompiler.3.0.0.201808031948Pro > sh ./jeb_macos.sh
2020-02-15 05:51:30.768 jeb[1807:69065] Failed to find library.:
2020-02-15 05:51:30.769 jeb[1807:69065] jeb:Failed to locate JNI_CreateJavaVM
2020-02-15 05:51:30.769 jeb[1807:69065] jeb:Failed to launch JVM
This may because the Jeb failed to locate the right JDK and on macOS or other unix-like system, java is determined through the /usr/libexec/java_home -V other than JAVA_HOME
Solve it
First Download the JDK on Oracle.
Then
/usr/libexec/java_home -V
Matching Java Virtual Machines (3):
12.0.1, x86_64: "OpenJDK 12.0.1" /Library/Java/JavaVirtualMachines/openjdk-12.0.1.jdk/Contents/Home
1.8.0_241, x86_64: "Java SE 8" /Library/Java/JavaVirtualMachines/jdk1.8.0_241.jdk/Contents/Home
1.8.0_222, x86_64: "AdoptOpenJDK 8" /Library/Java/JavaVirtualMachines/adoptopenjdk-8.jdk/Contents/Home
Write
<key>JVMCapabilities</key>
<array>
<string>CommandLine</string>
<string>JNI</string>
<string>BundledApp</string>
</array>
to /Library/Java/JavaVirtualMachines/jdk1.8.0_241.jdk/Contents/Info.plist
sudo mkdir -p /Library/Java/JavaVirtualMachines/jdk1.8.0_241.jdk/Contents/Home/bundle/Libraries
sudo ln -s /Library/Java/JavaVirtualMachines/jdk1.8.0_241.jdk/Contents/Home/jre/lib/server/libjvm.dylib /Library/Java/JavaVirtualMachines/jdk1.8.0_241.jdk/Contents/Home/bundle/Libraries/libserver.dylib
To check
/usr/libexec/java_home -t BundledAPP
/Library/Java/JavaVirtualMachines/jdk1.8.0_241.jdk/Contents/Home
Done
sh ./jeb_macos.sh
Memory Usage: 61.5M allocated (20.5M used, 41.0M free) - max: 910.5M
JEB v3.0.0.201808031948 (release/full/individual/air-gap/any-client/core-api)
Current directory: /Users/yiweiyang/Downloads/JEB.android.decompiler.3.0.0.201808031948Pro/bin/jeb.app/Contents/Java
Base directory: /Users/yiweiyang/Downloads/JEB.android.decompiler.3.0.0.201808031948Pro
Program directory: /Users/yiweiyang/Downloads/JEB.android.decompiler.3.0.0.201808031948Pro/bin
System: Mac OS X 10.15.2 (x86_64) en_CN
Java: Oracle Corporation 1.8.0_241
Plugin loaded: com.pnf.plugin.oat.OATPlugin
Plugin loaded: com.pnf.androsig.gen.AndroidSigGenPlugin
Plugin loaded: com.pnf.androsig.apply.andsig.AndroidSigApplyPlugin
Plugin loaded: com.pnf.plugin.pdf.PdfPlugin
用cuda破解ZIP存档密码
jabrown在2017年10月30日星期一提交-01:51
这将是有关如何破解受密码保护的ZIP档案的快速演练。
您将需要Hashcat和John Ripper大号。
如果使用的Linux系统没有zip2john软件包,则John Jumbo将需要编译。
将Hashcat和Ripper拆封并编译后,我们就可以获取ZIP文件的哈希值。
要获取哈希值,请运行。 / path / to / john / jumbo / run / zip2john {zip文件}

这将创建一个以冒号(:)分隔的字符串。我们仅在使用Hashcat破解哈希值时使用哈希值。
创建仅使用哈希值运行的哈希列表。 / path / to / john / jumbo / run / zip2john {zip文件} | cut -d':'-f 2> {哈希列表文件}

一旦有了哈希值,便可以使用Hashcat对其进行破解。
Hashcat命令对Winzip哈希使用单词列表攻击。 hashcat -a 0 -m 13600 {哈希列表} {wordlist}
由于Linux内核,GPU驱动程序和哈希破解系统的硬件的独特问题,我们使用的命令有所不同。
hashcat
只需几秒钟即可破解“ password”的简单密码。
拉链裂纹
使用正确的工具和单词列表,轻松破解ZIP密码非常容易。
上科大逻辑与形式化验证讲座3
Explicit-State Model Checking
Breadth-first Search
- X!y: add y as the last element of X
- X!!y: add y as the first element of X
- X?y: remove the first element of X as y
Depth-first Search
Nested Depth-First Search
- dfs from a reachable final state to check if a loop exists
Bitstate Hashing
Binary Decision Diagrams
- (X0 && ! X1) || (X0 && X1) == X0
- Boolean Function API
- A BDD represents a Boolean function as an acyclic directed graph
- Nonterminal vertices labeled by Boolean variables
- Leaf vertices labeled with the values 1 and 0
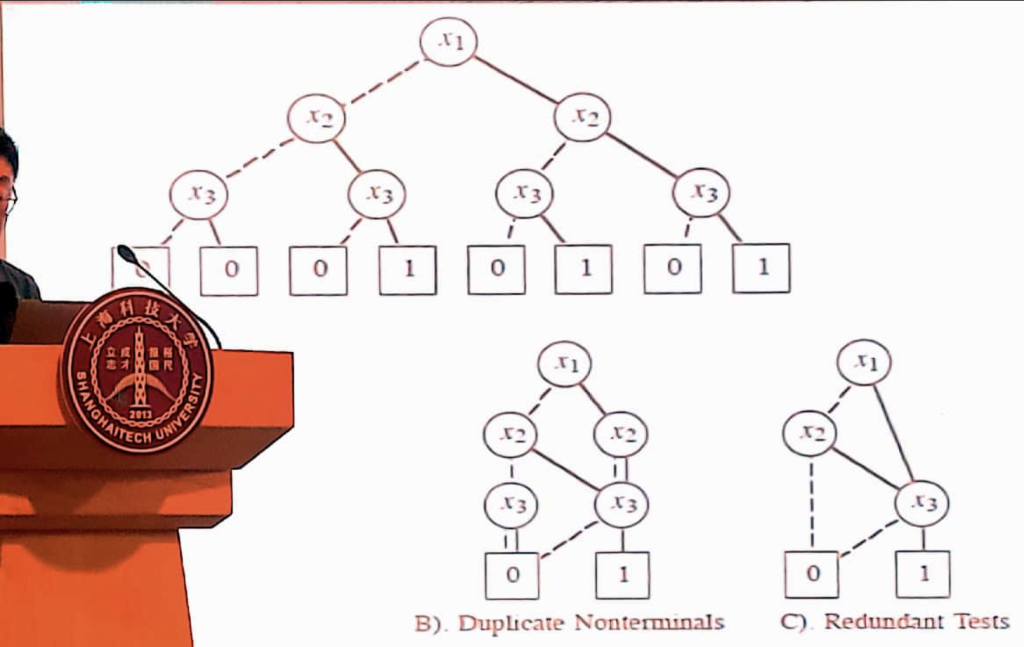
- Restrict(f,i,b):
- R(x1 && x2, 1, True) == x2
- …

BDD-based symbolic model checking
- represent sets of state
- represent transition relation
- p’: p of next state
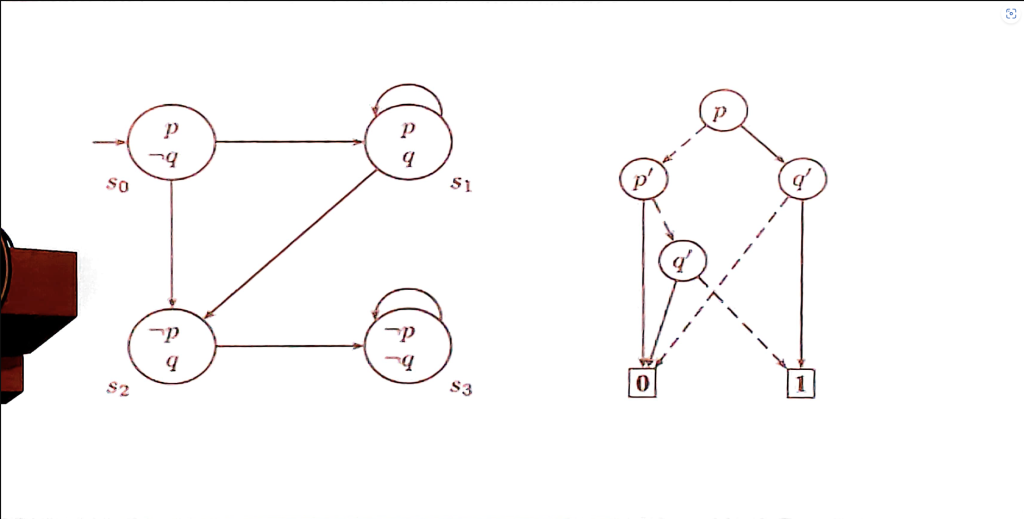
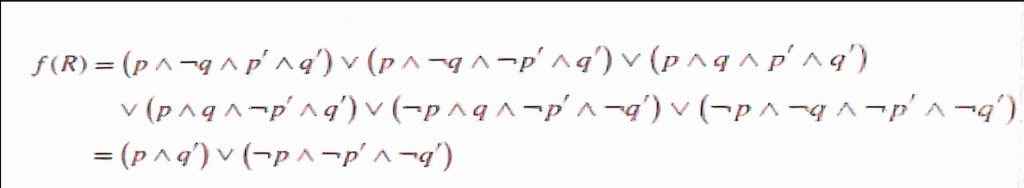
- BddImage & BddPreImage
上科大逻辑与形式化验证讲座
时间逻辑与模型检查
克里普克结构
K=
符号逻辑
自然语言:
模棱两可的
悖论
代数逻辑
时间逻辑控制*
路径量词
A:对于此状态的每个无限路径(任意路径中的状态)
E:这个状态有一条无限的路径
时间运算符
xp:p保持在下一个状态
FP:P在未来的某些州持有
gp:p将来在所有州都持有
qup:fp,q在所有状态下保持,直到p保持。
时间逻辑控制
A、E和E、F、G、U必须成对站立
时态逻辑LTL(线性时态逻辑)
不e
只有一条路
算法挑战
对称性约简
飞行状态空间探索
部分降阶
假设保证推理
符号方法
BDD
抽象
模型检查的未来
合成(根据规范生成程序)
归纳、模型测量
人工智能????
建模软件
断言
转换:
启用条件:预测
转换:多重分配
A>B->(B,C):=(C,D)
执行:状态序列
LTL
☐盒子,永远,G
:钻石,最终,F
:下一个时间,x
有限词上的自动机
自动机
非确定性
确定性
正确性条件
我们希望找到一个模型满足规范的正确性条件。
模型语言:L(模型)
规范语言:L(规范)
我们需要:L(型号)L(规格)
程序执行符合规范的序列所有序列

