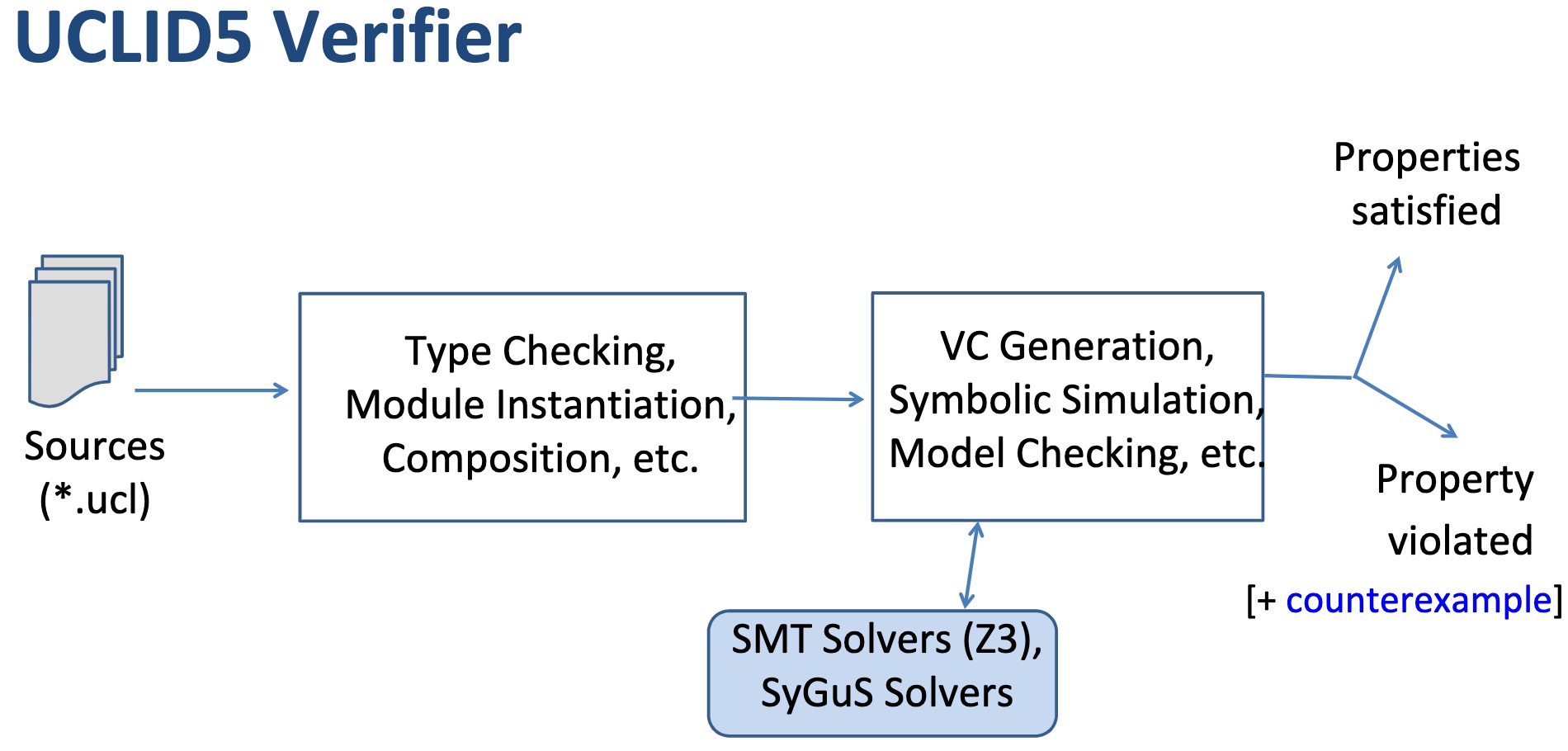
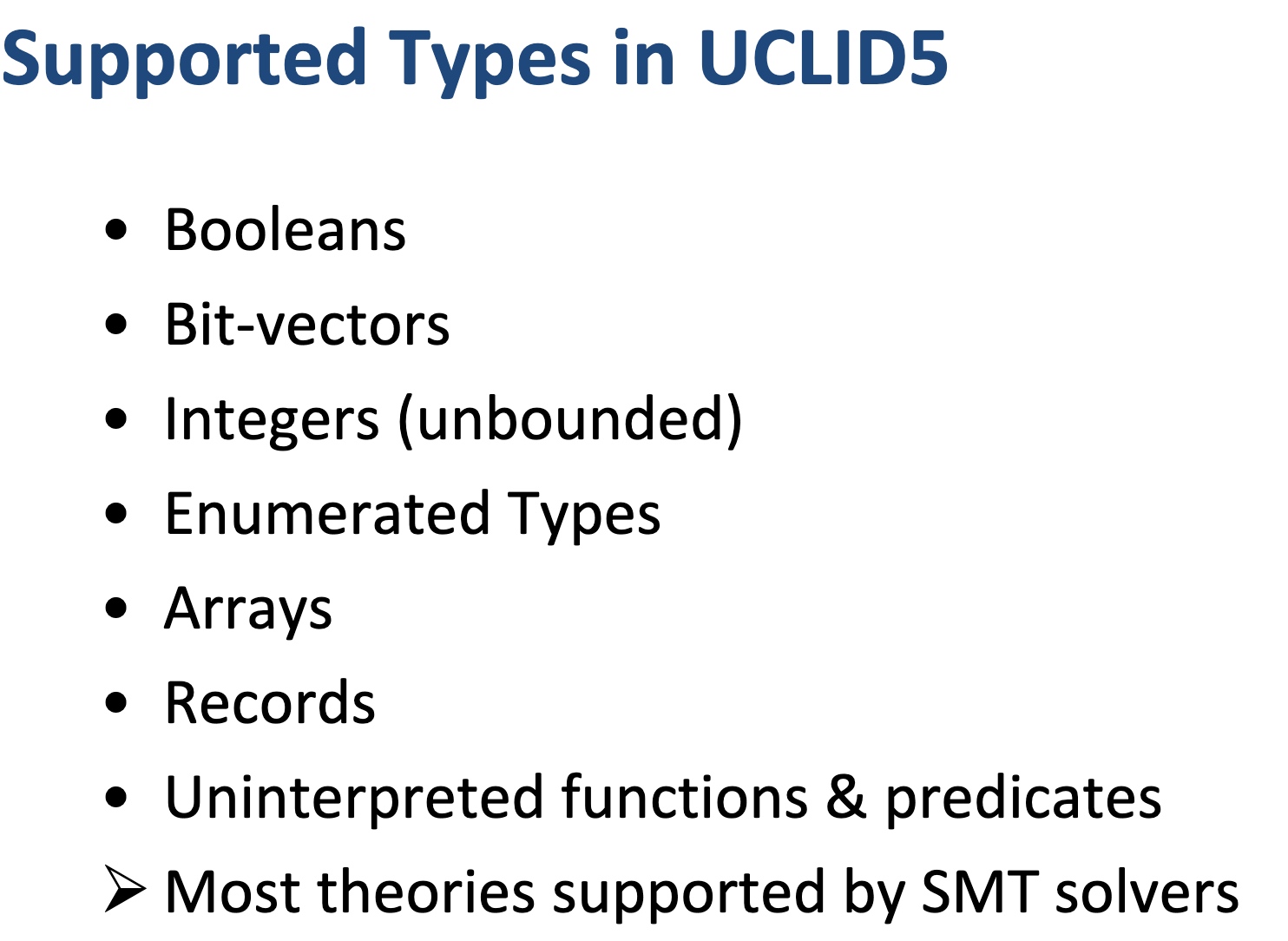
When I was browsing keystones‘ paper, they are applying a verification model called UCLID5, a new software toolkit based on z3 written in scala for the formal modeling, specification, verification, and synthesis of computational systems. The augmented efforts are merely making architectural implementations like NAPOT/S mode world change/exceptions in pmp reg mapping policy to Hoare logic and do the verification. To a greater extent, the Y86-64 introduced in CSAPP is verified by UCLID5, too.

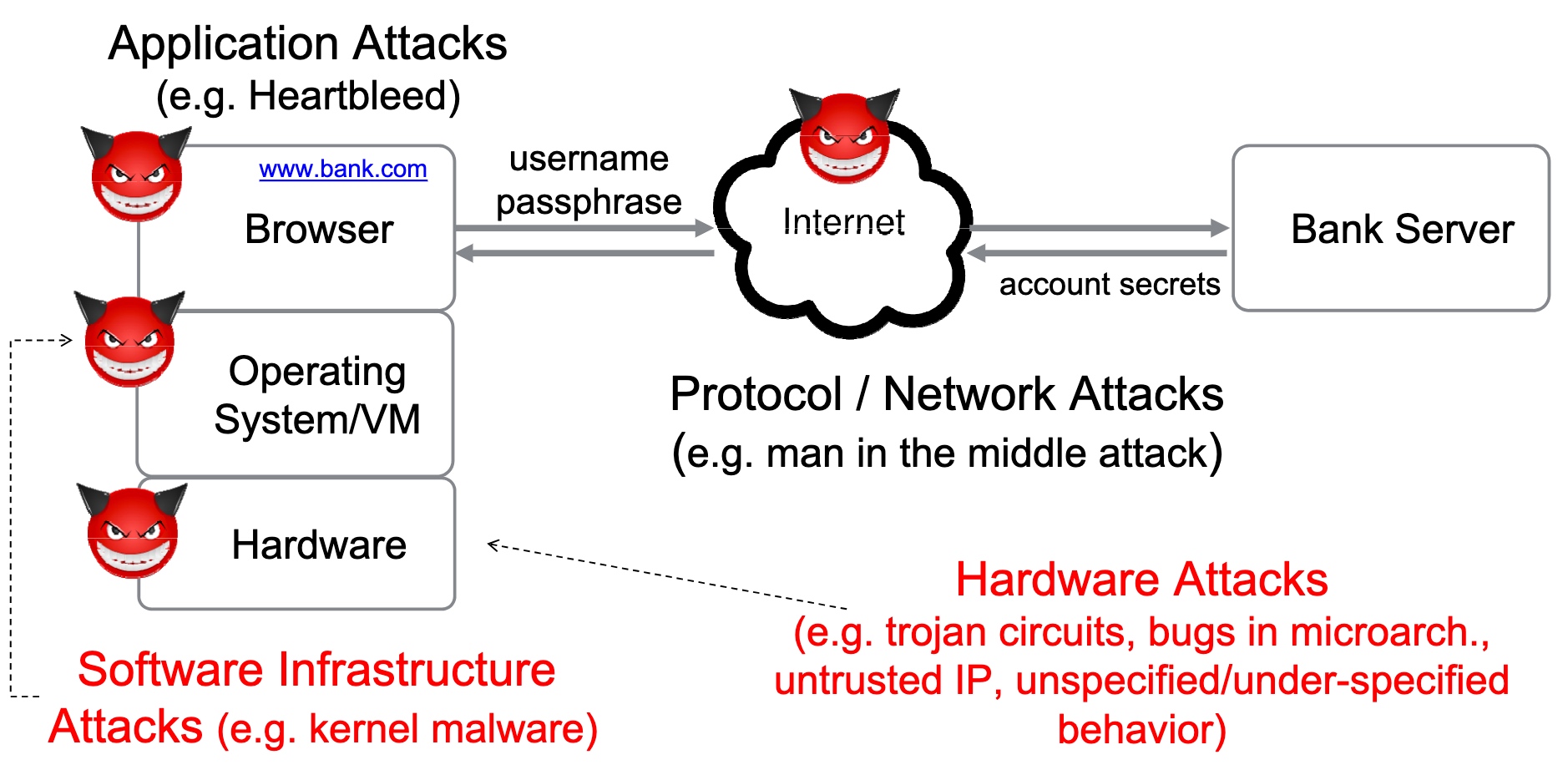
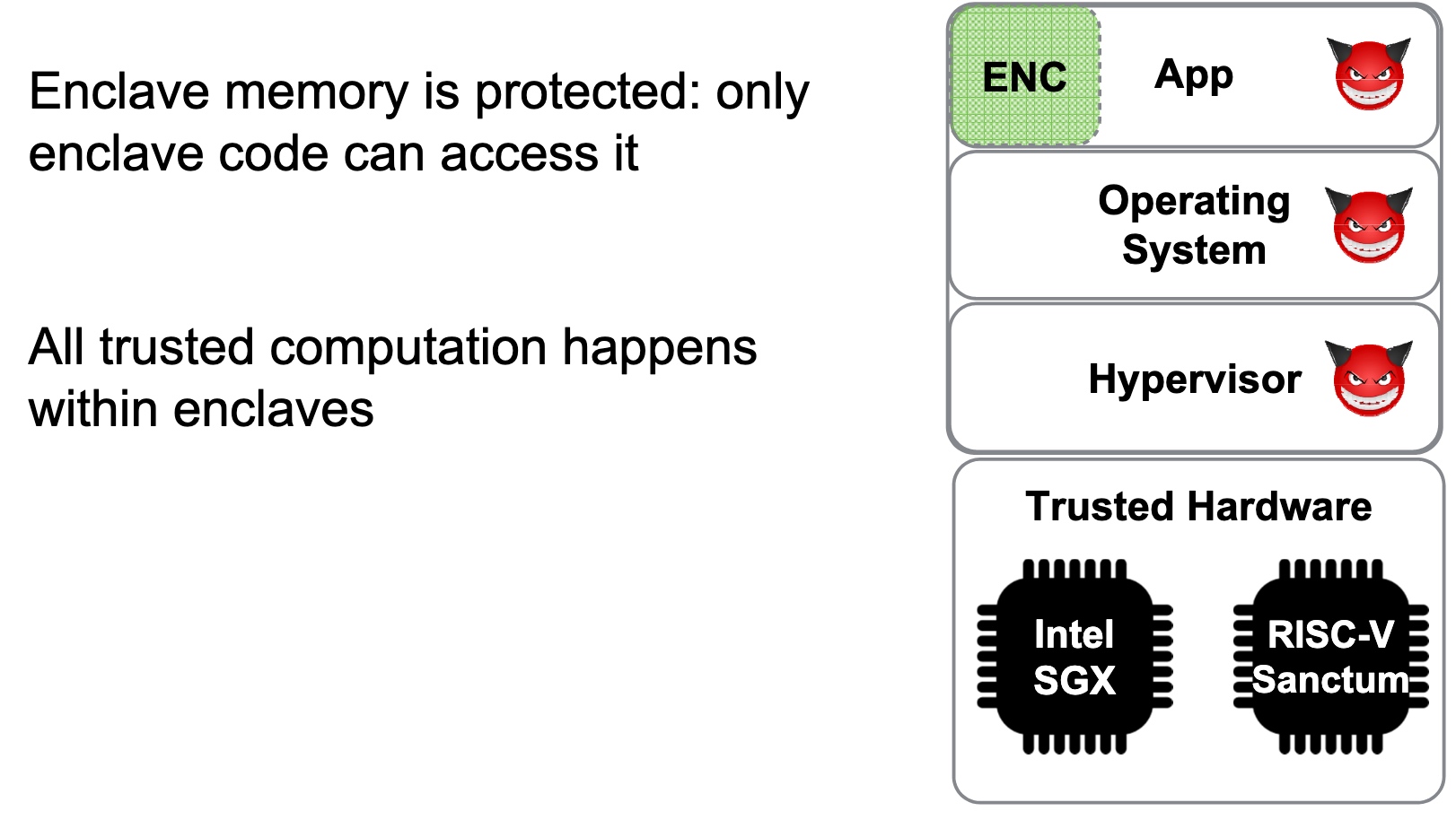
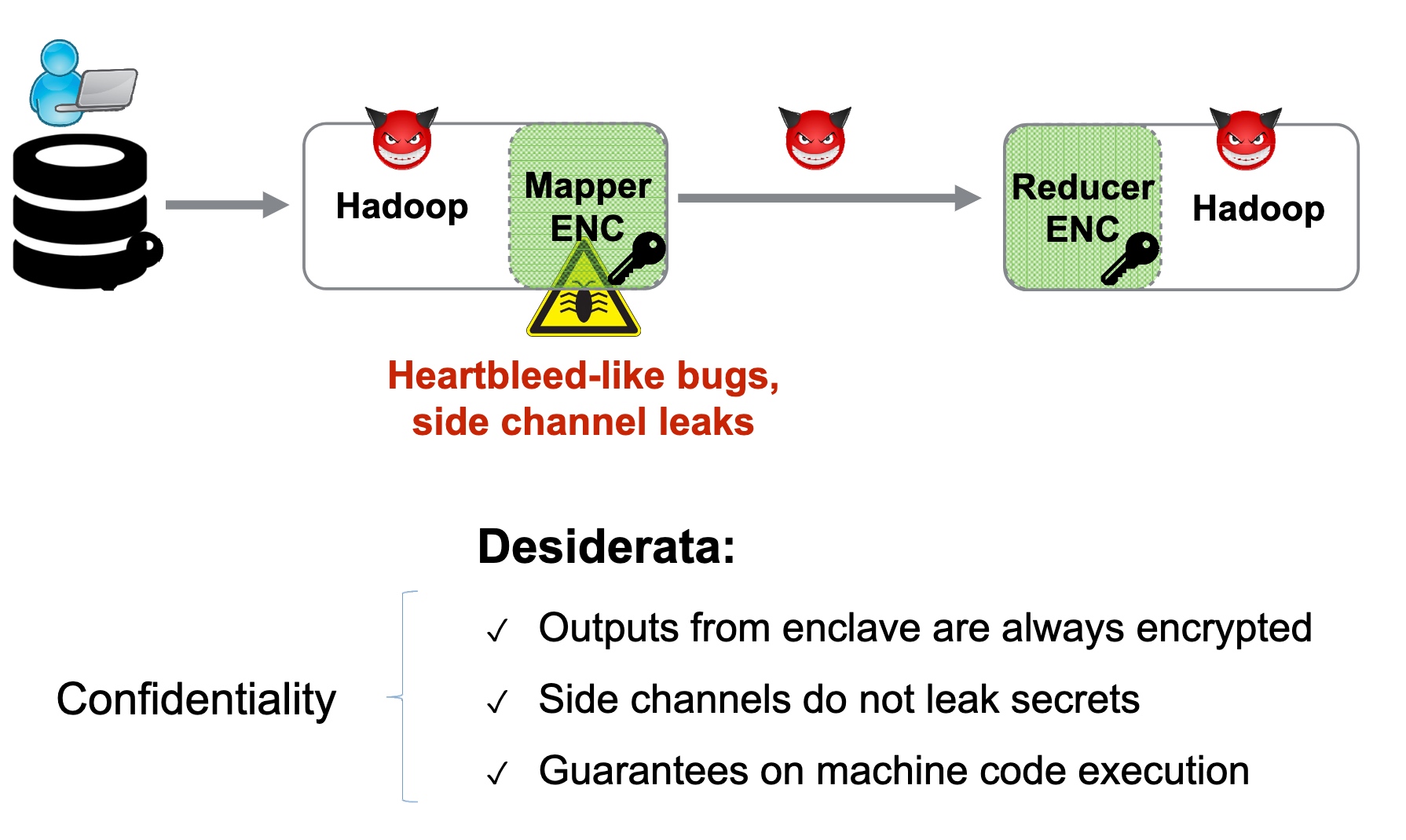
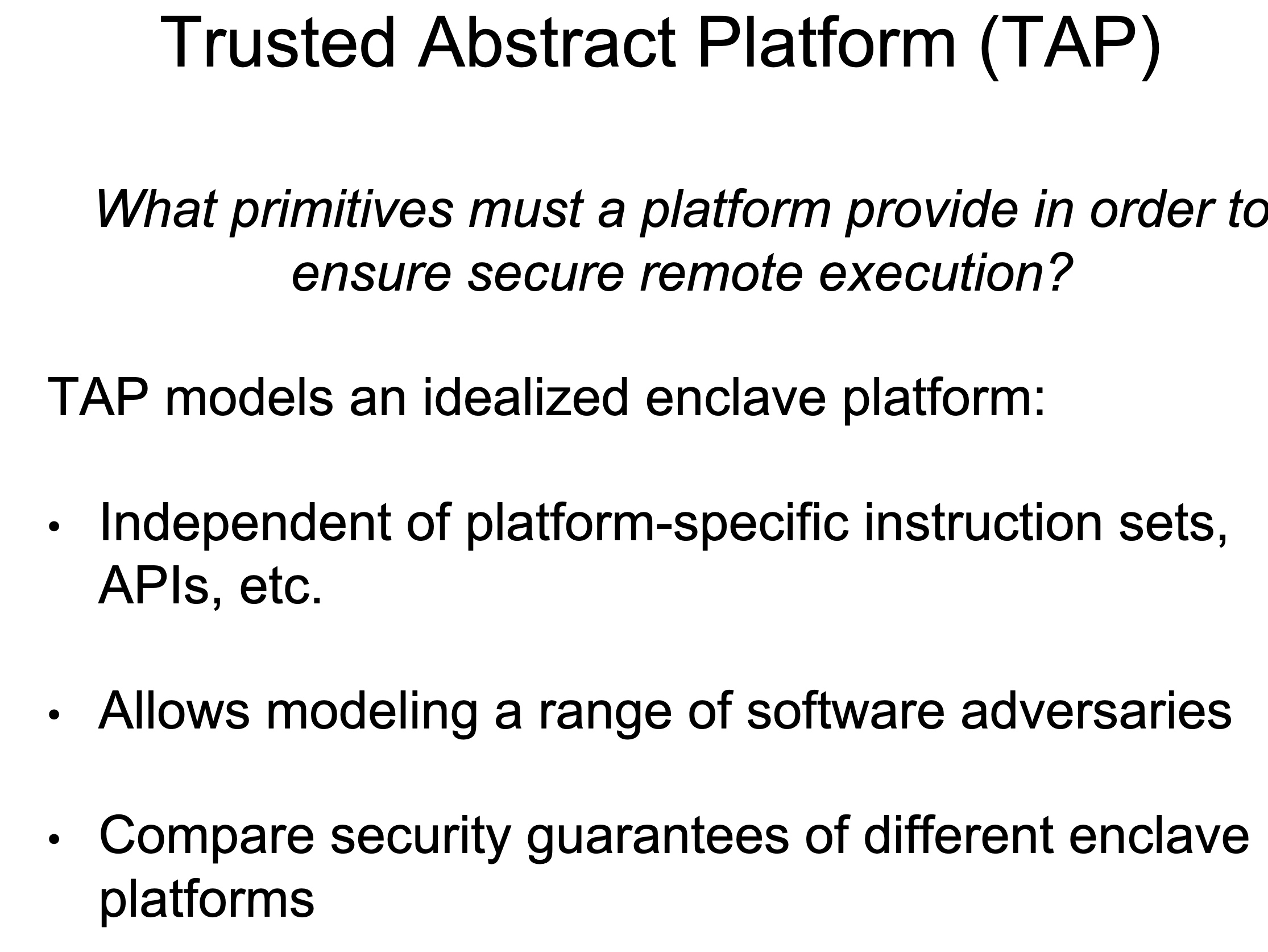
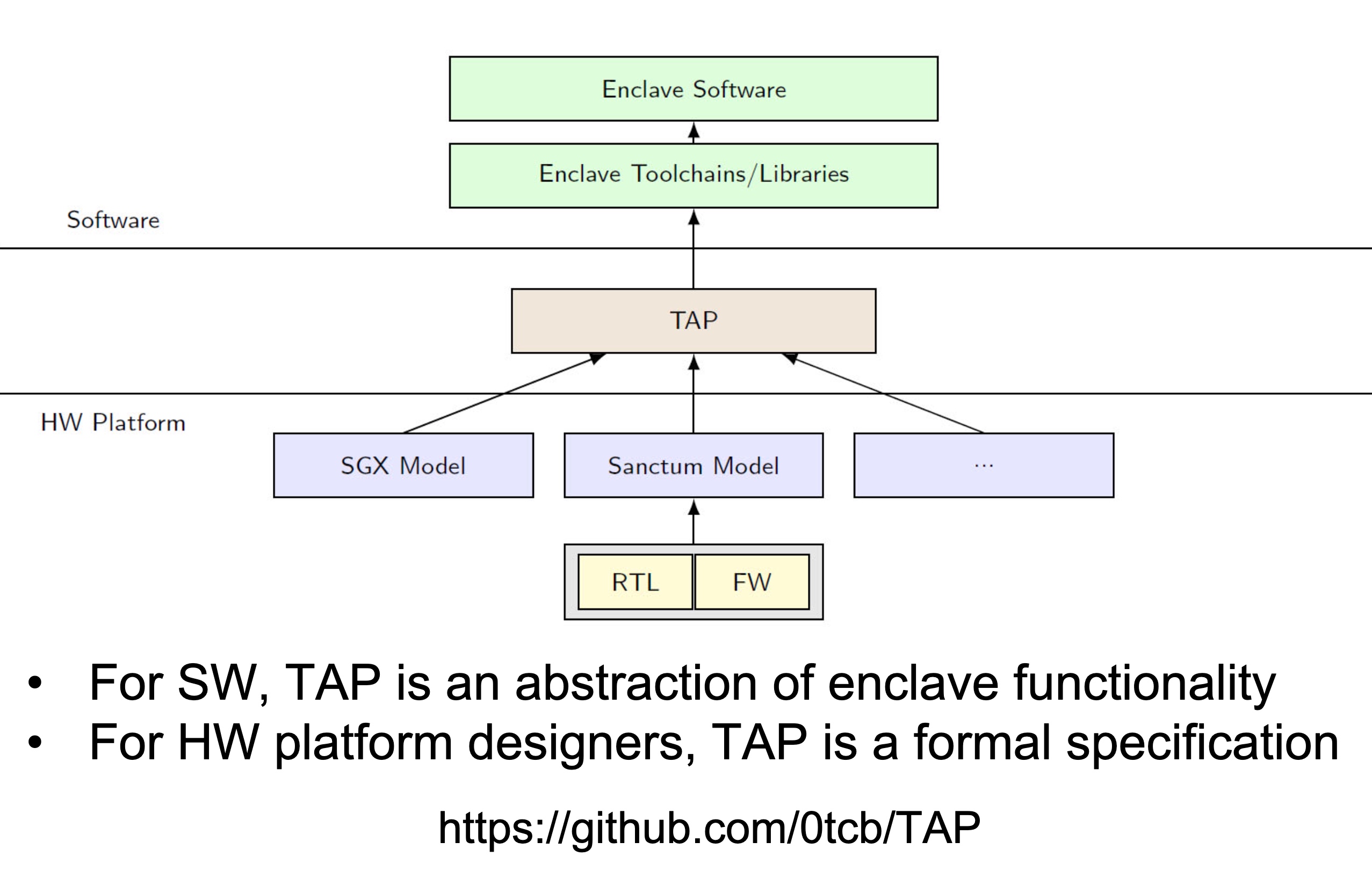
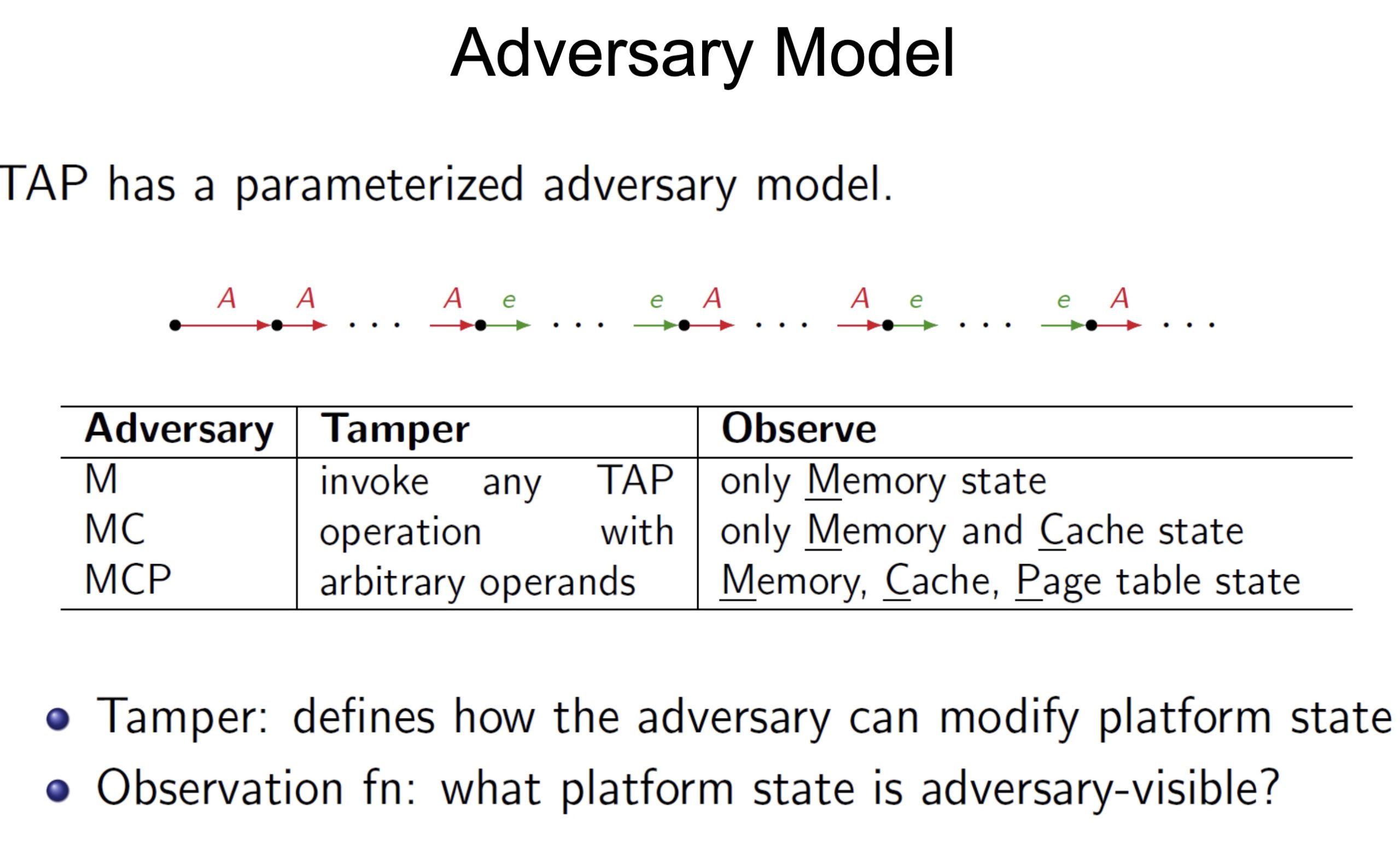
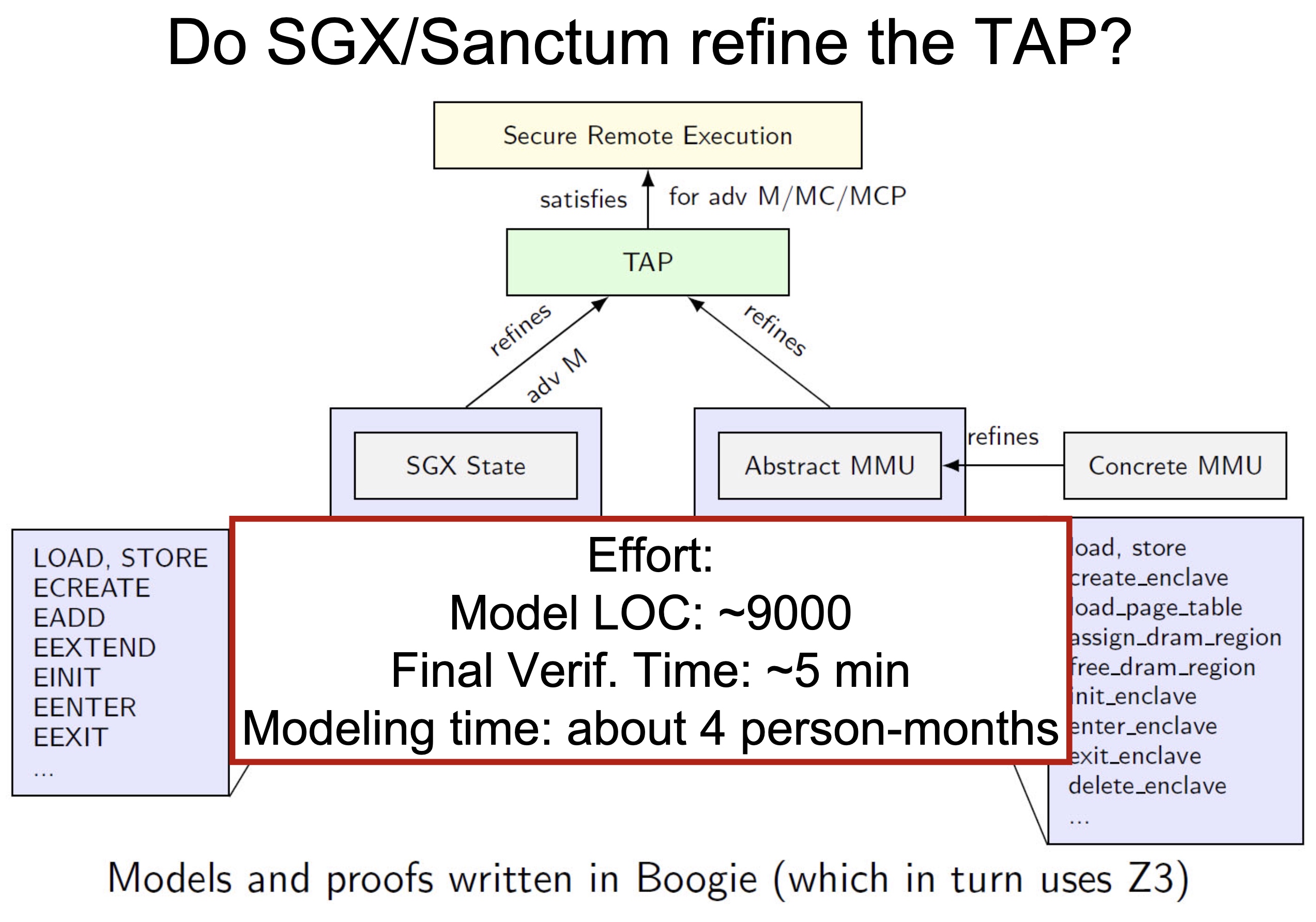
Heartbleed-like attack, side channels, and Meltdown/Spectre are also cast a lot on SGX/TEE. Stuff like secure remote extensions using trusted platforms is introduced. They formalized the enclave platform and made remote execution trustworthy.
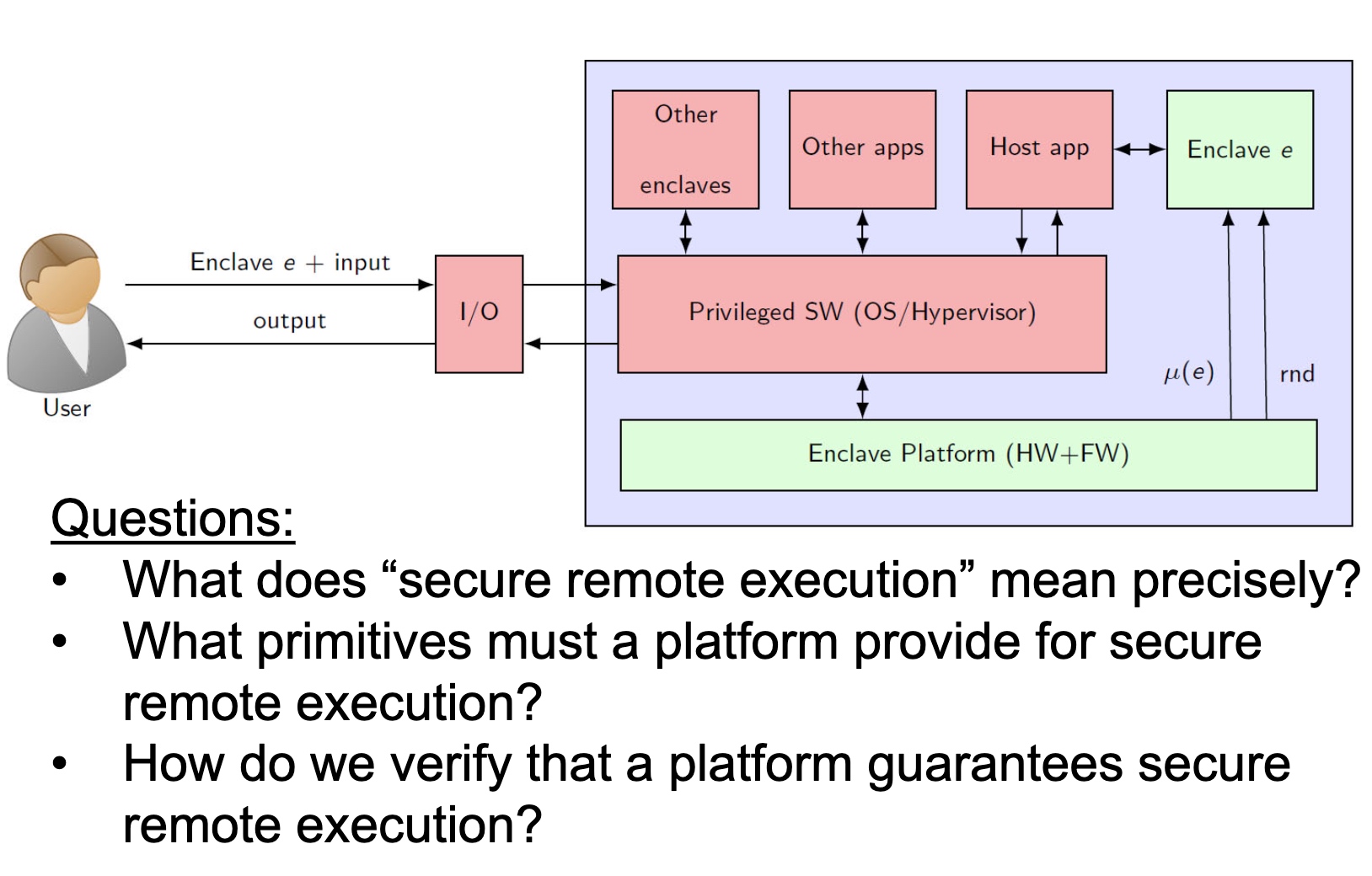


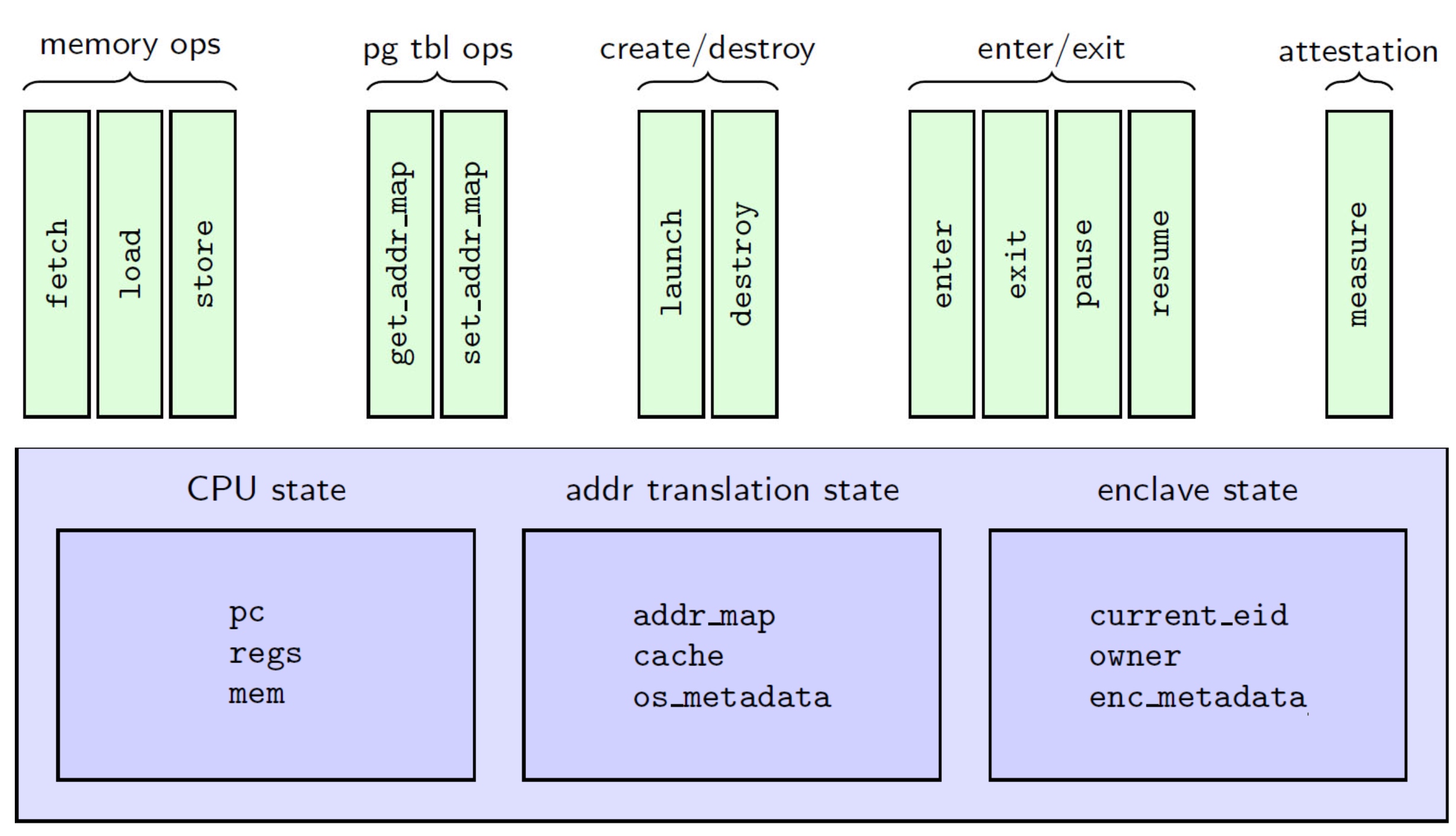

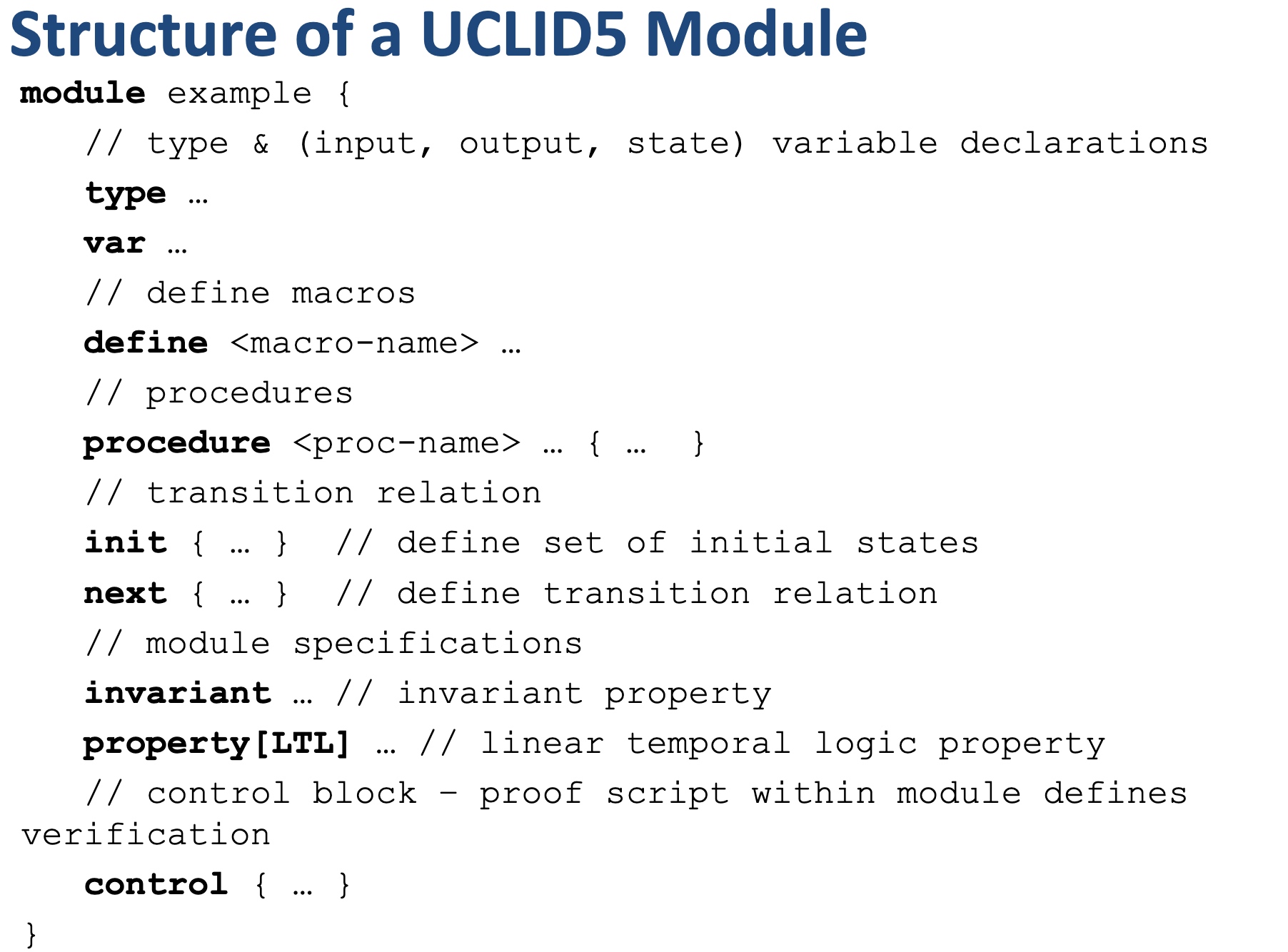
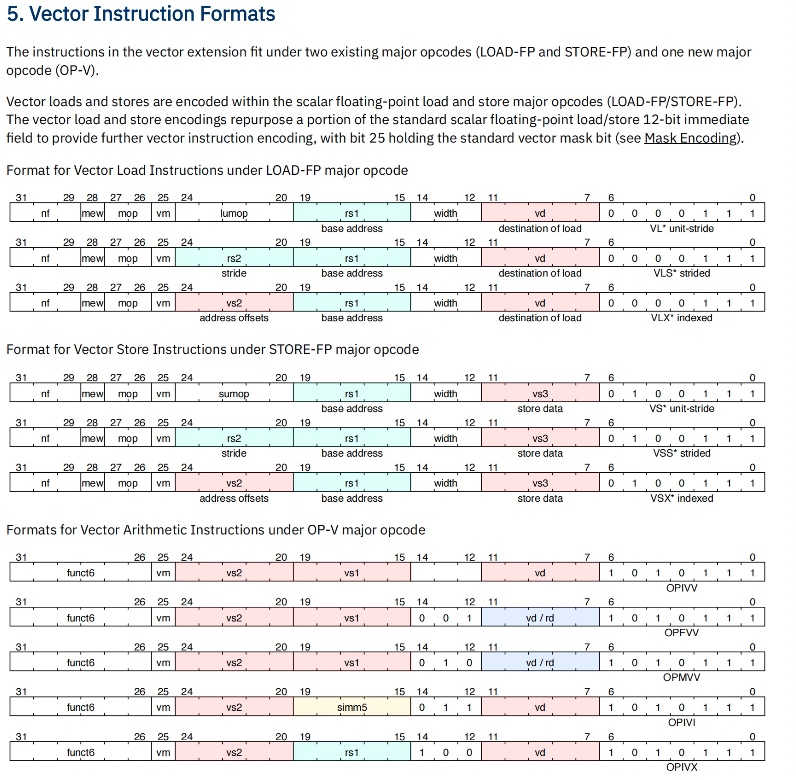
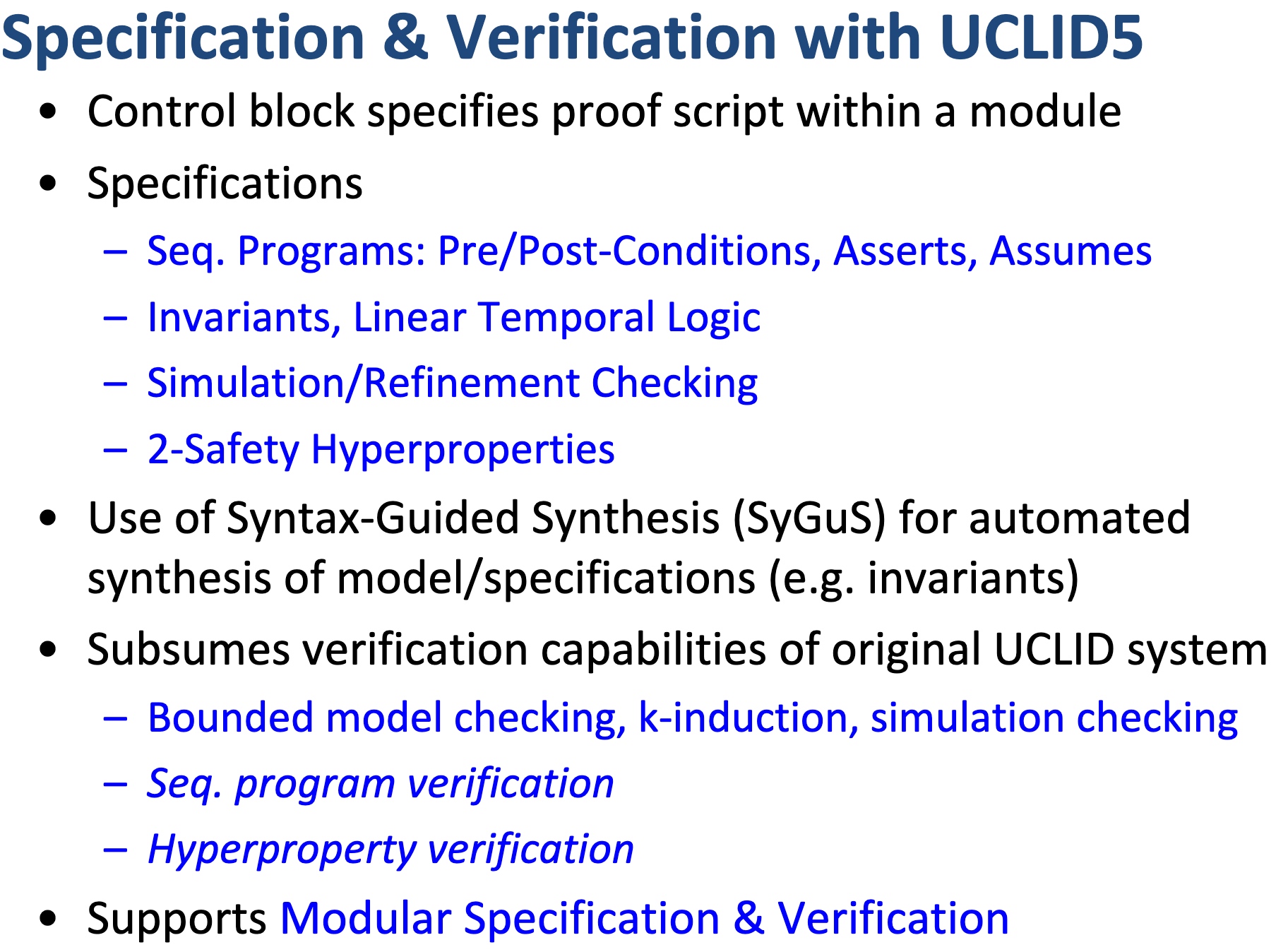
Modules, like LLVM, serve as the unit of re-use when declaring commonly used types, symbolic constants, and uninterpreted functions. The module uses uninterpreted functions to model instruction decoding (inst2op, inst2reg0 etc.) and instruction execution (aluOp and nextPC). Further, the register file index type (regindex_t) and the address type (addr_t) are both uninterpreted types. This abstraction is sufficient to model all kinds of CPU implementation.
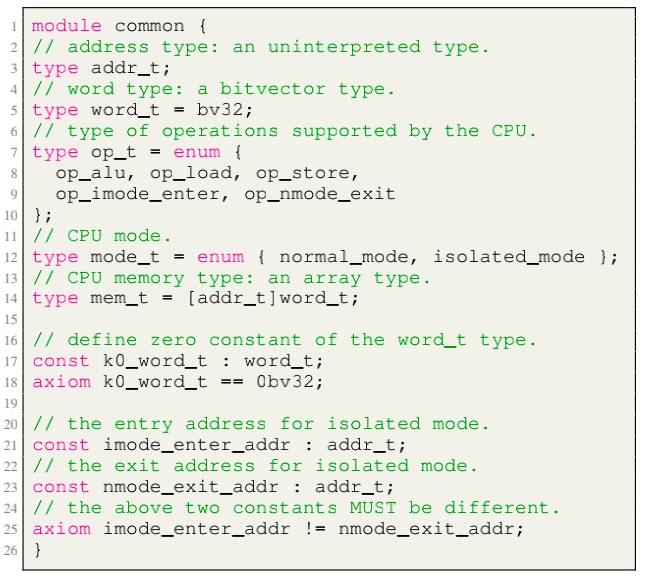
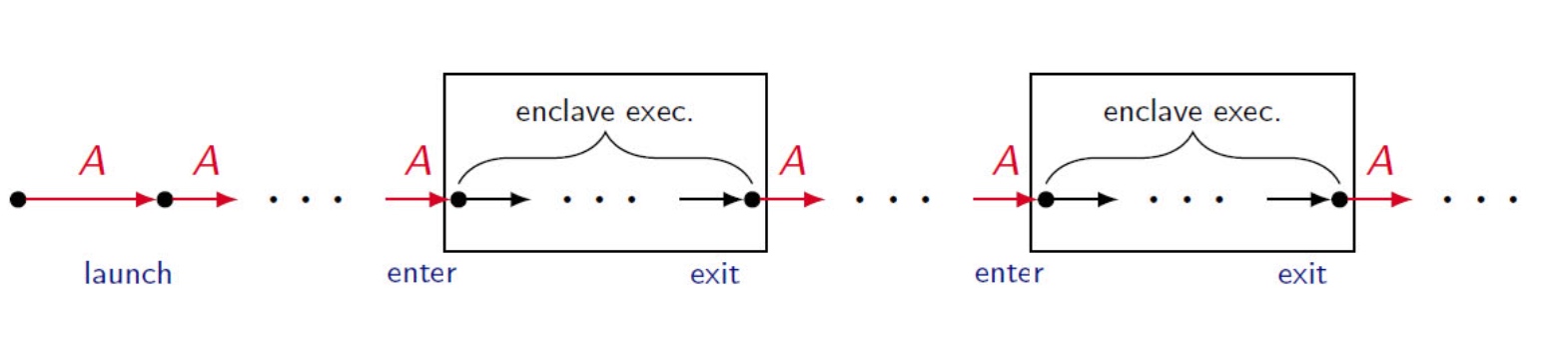
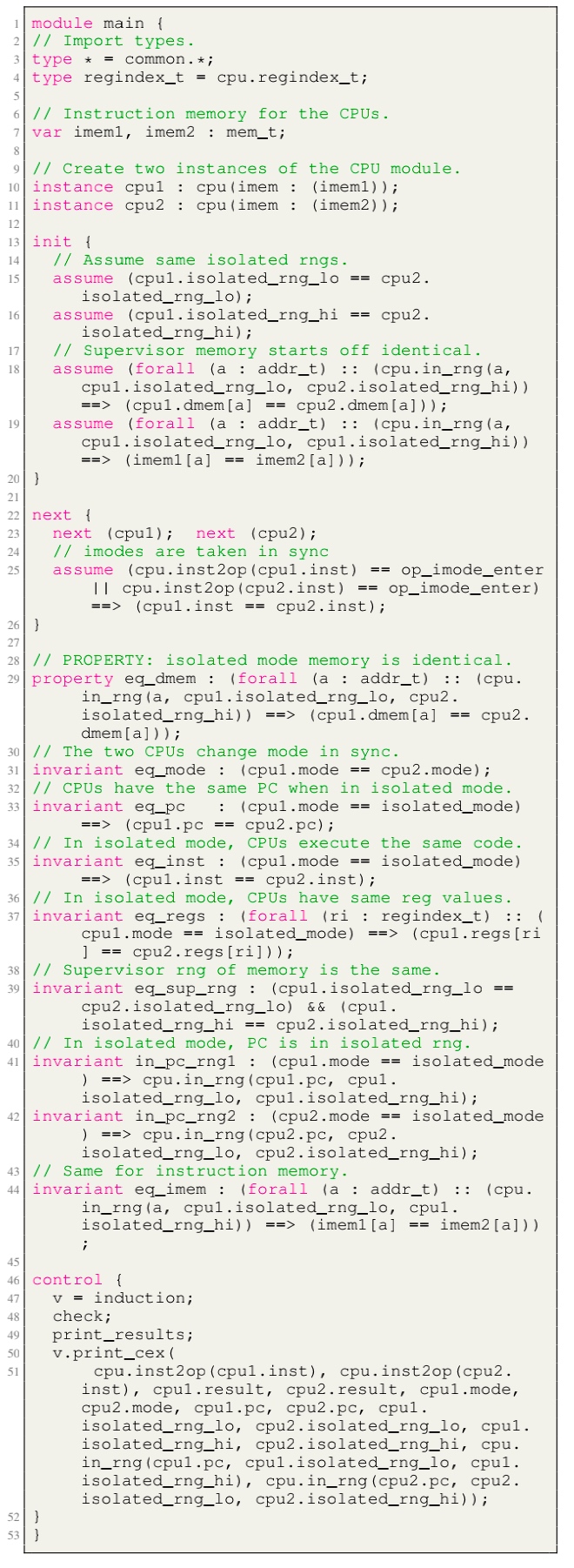
isolated_rng_lo and isolated_rng_hi) init/next/exec_inst defines the transition system.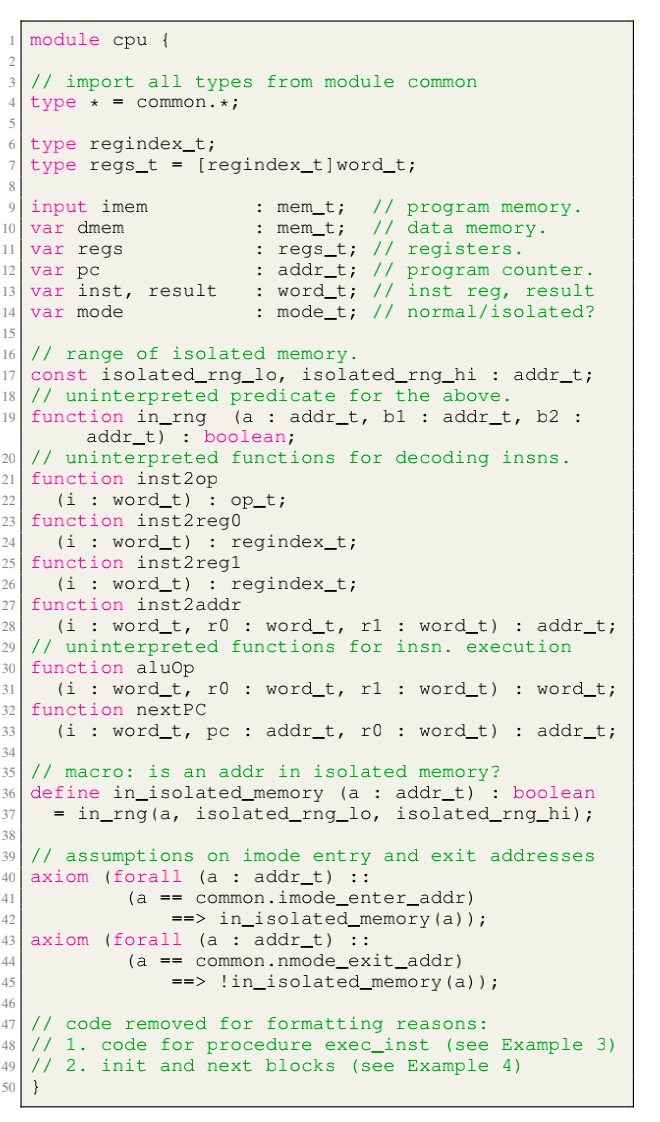

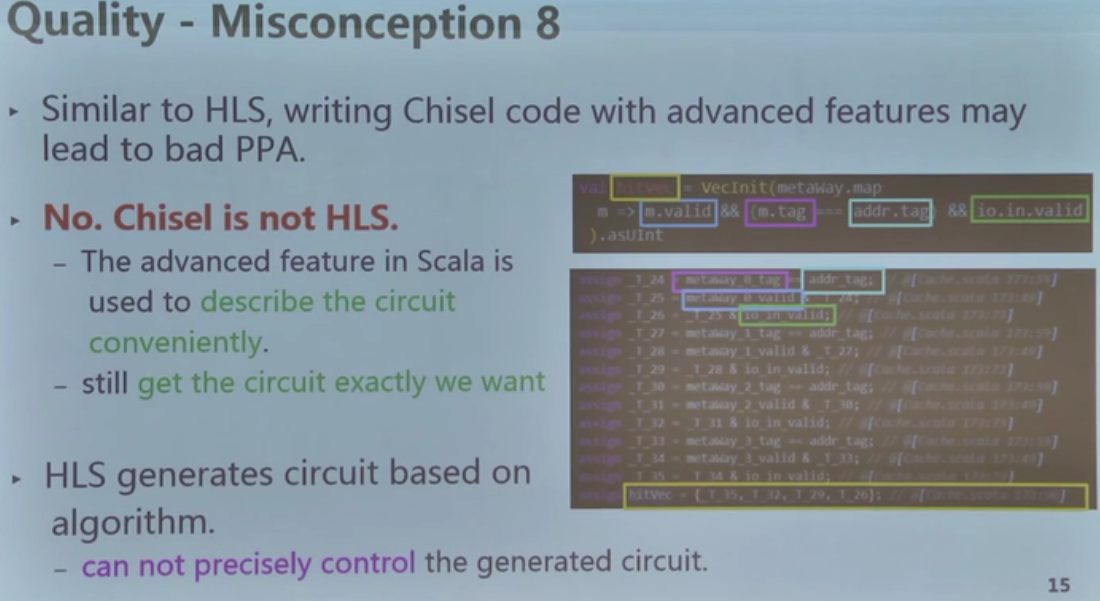
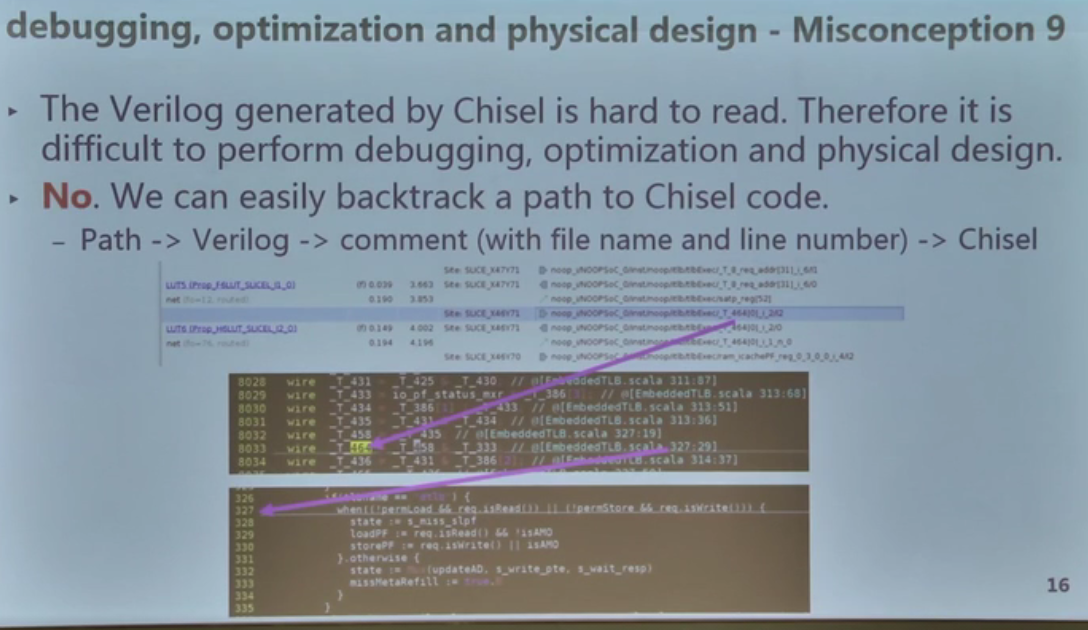
板级驱动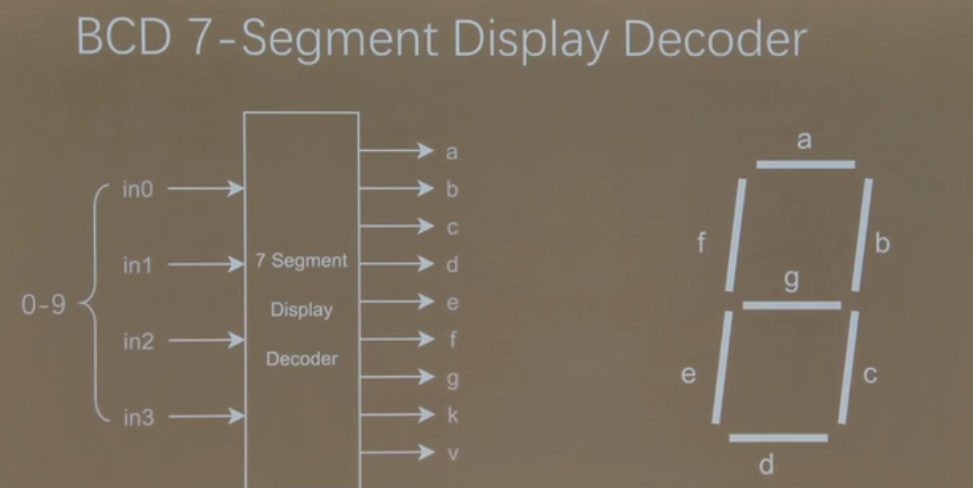
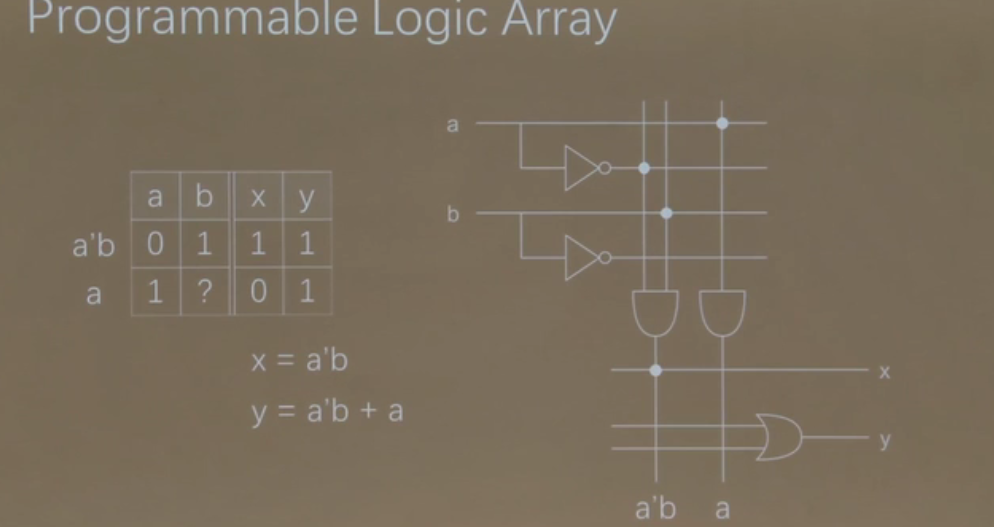
chisel ALU
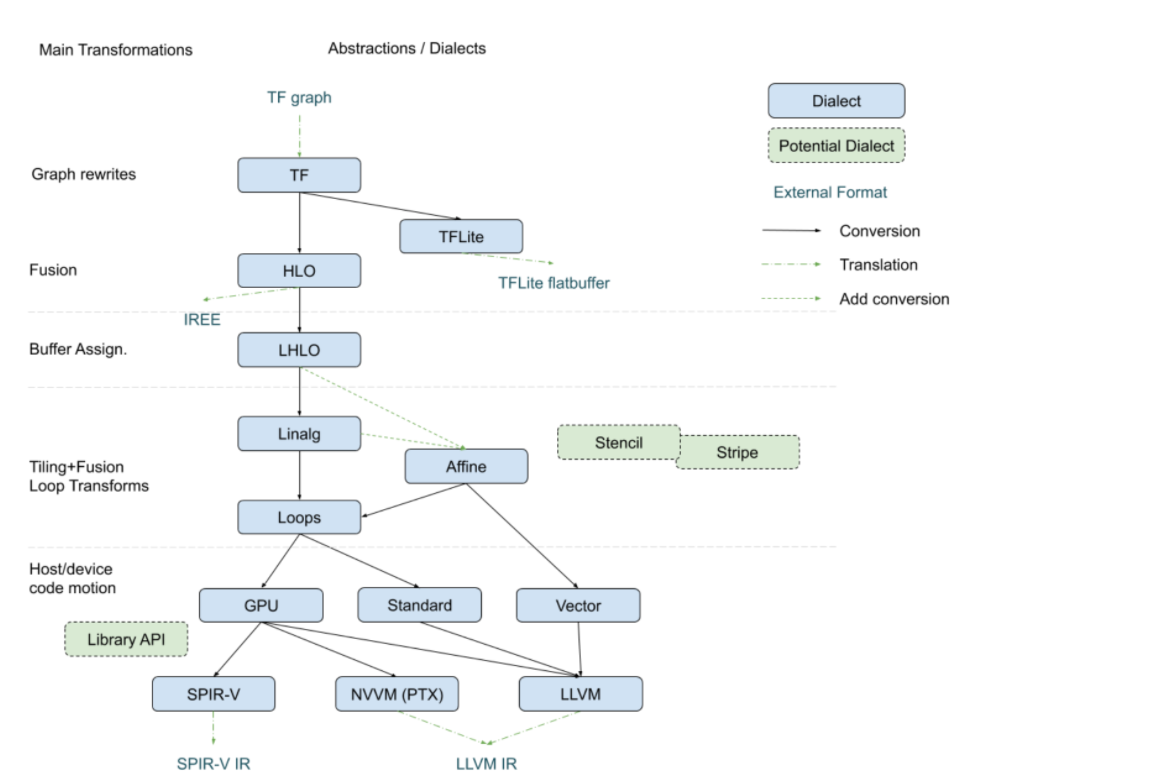
buddy-mlir
可重构计算 - 用chisel构建 tweaked DSL based on C
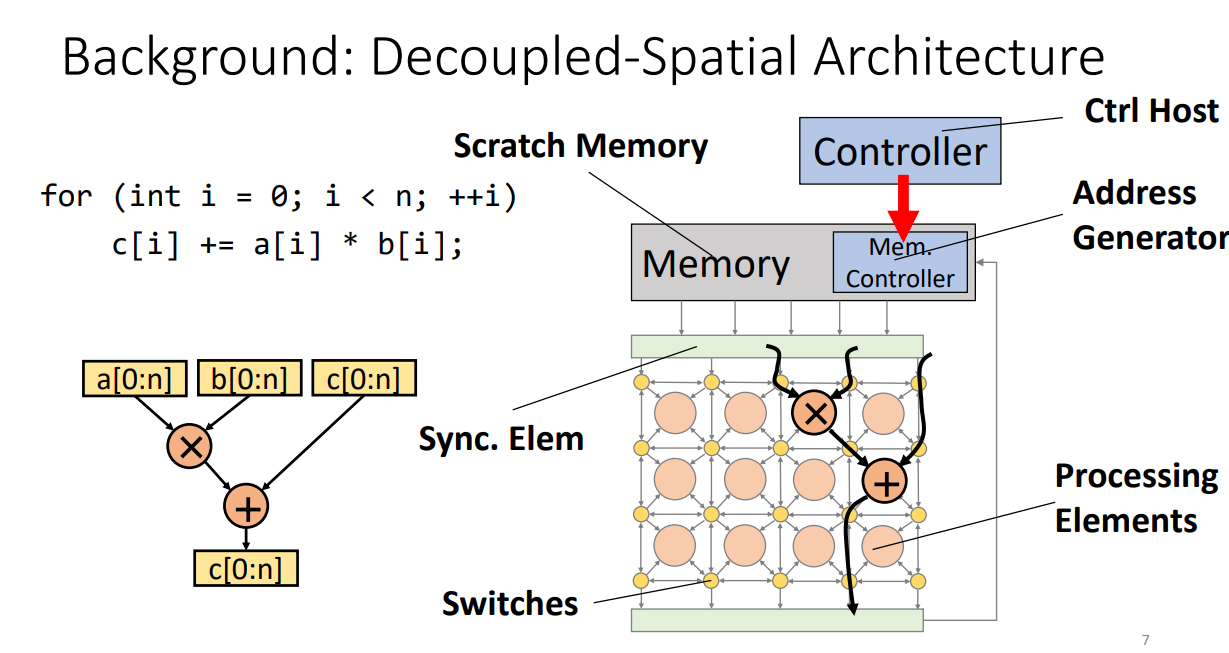
The overlay generation: workloads MachSu.
The circuit and Rocket Core mapped onto Kernel vector
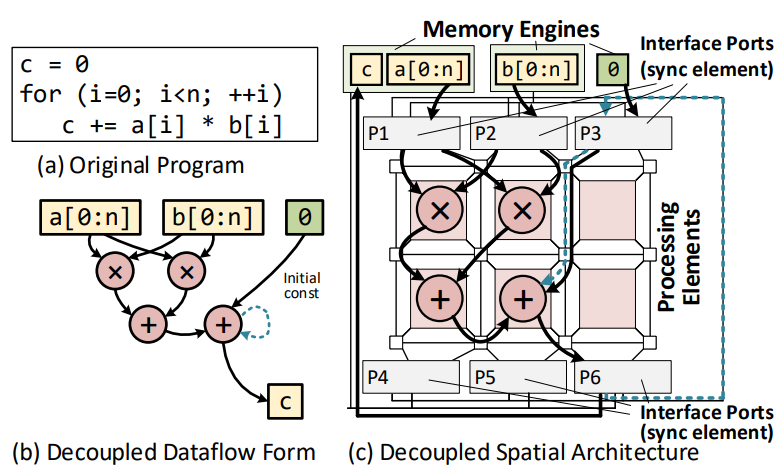
DSOGEN Process on Hardware Side
从硬件上完成Hardwareside 的compiler
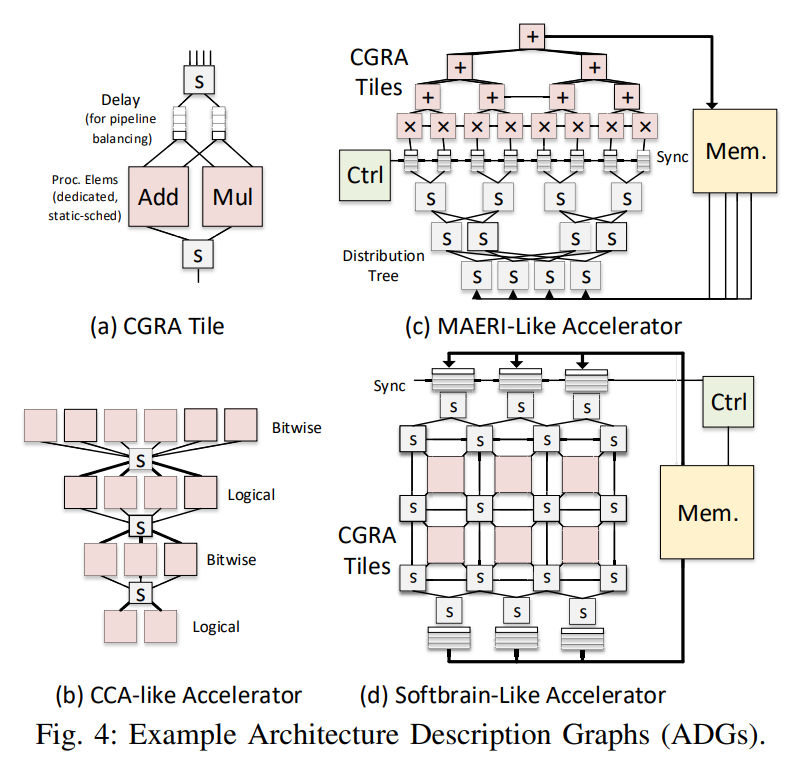
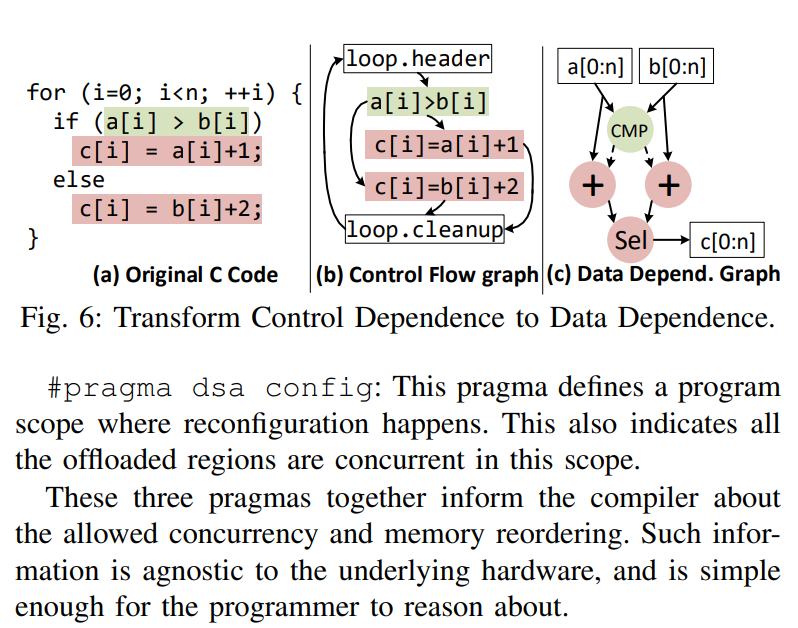
Control flow implementation
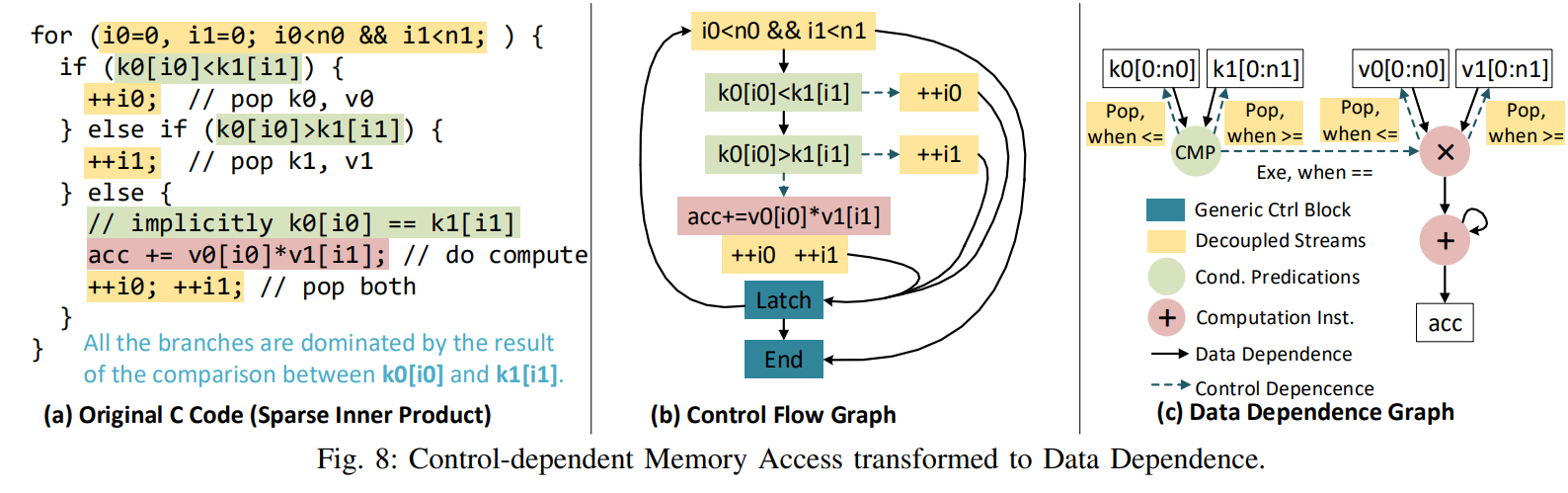
Better tahn AutoDSE of HLS
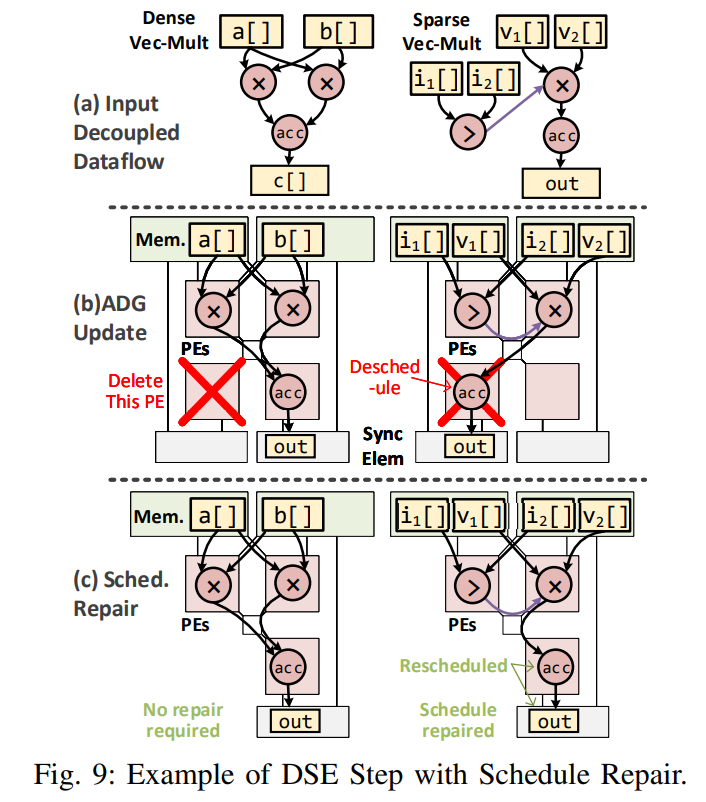
current Vitus 设计空间探索。
图计算加速
PolyGen FPGAF1
高性能

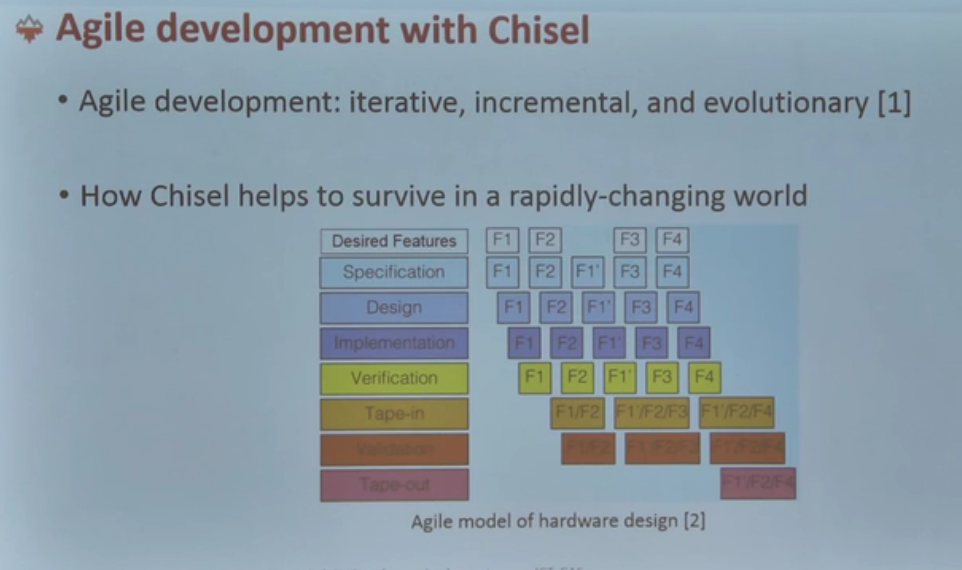
Poly graph
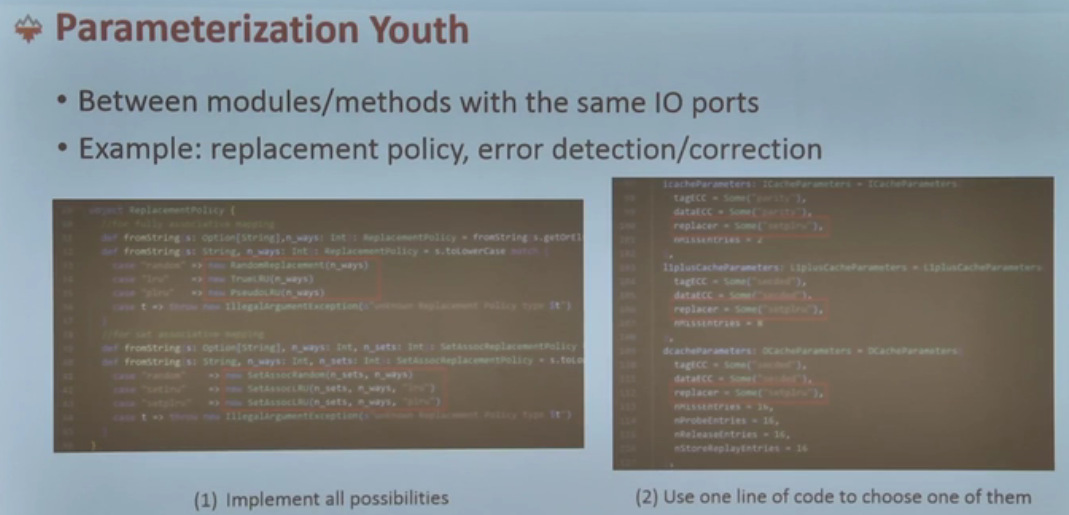

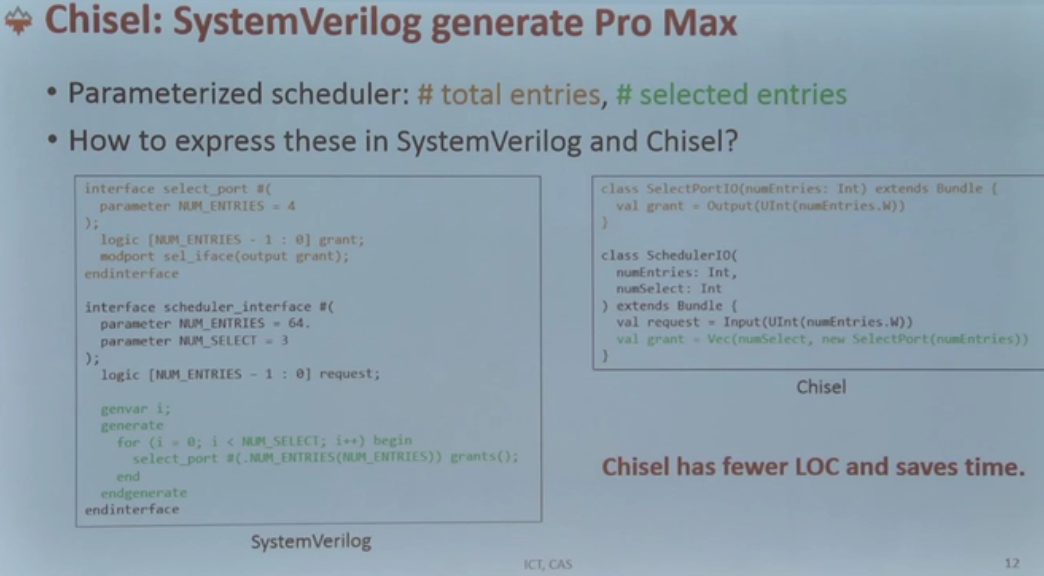
一个中国chisel 之父,但对人真的很好。
gnu test 的优点
Gentoo 发行版的发布
自动化测试
libfuzzer
CKB-VM
密码学xdwrite
一维流式结构
riscv
树状结构
riscv+gas 模型
内存延时初始化
密码学算法 K extension