文章目录[隐藏]
Efficient reconstruction techniques for disaster recovery in secret-split
Use secret split. The assumption is shards with different authentication ways will be safe without encryption by only matching. And the guard will identify the attacks when the attacker's operation is great enough.
Approximate pointer, use whole sharding for recovery to prevent the adversarial
64 - 64 - 64
\ 64 \ 64
... ...
Different approaches for the secret split. one get diverged from the list of key, the other uses a 128-bit field that will not leak information of the key.
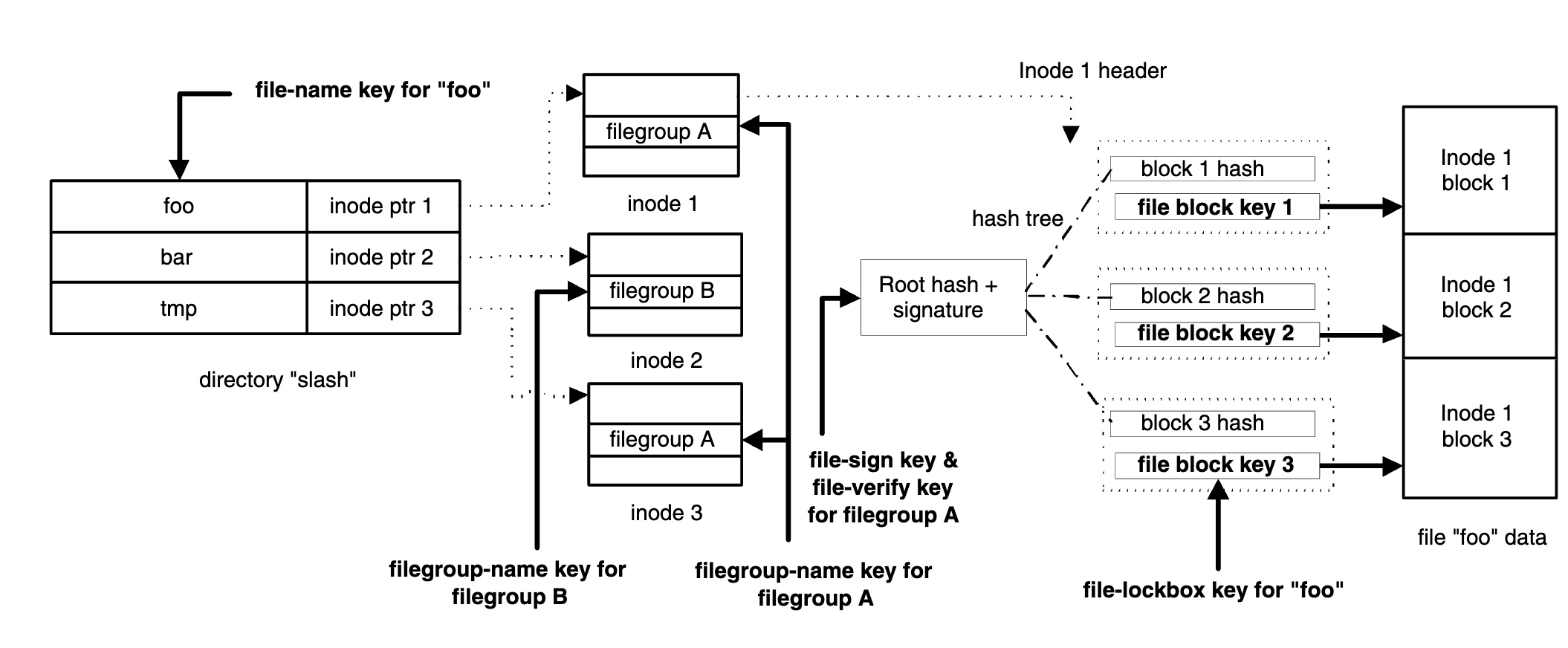
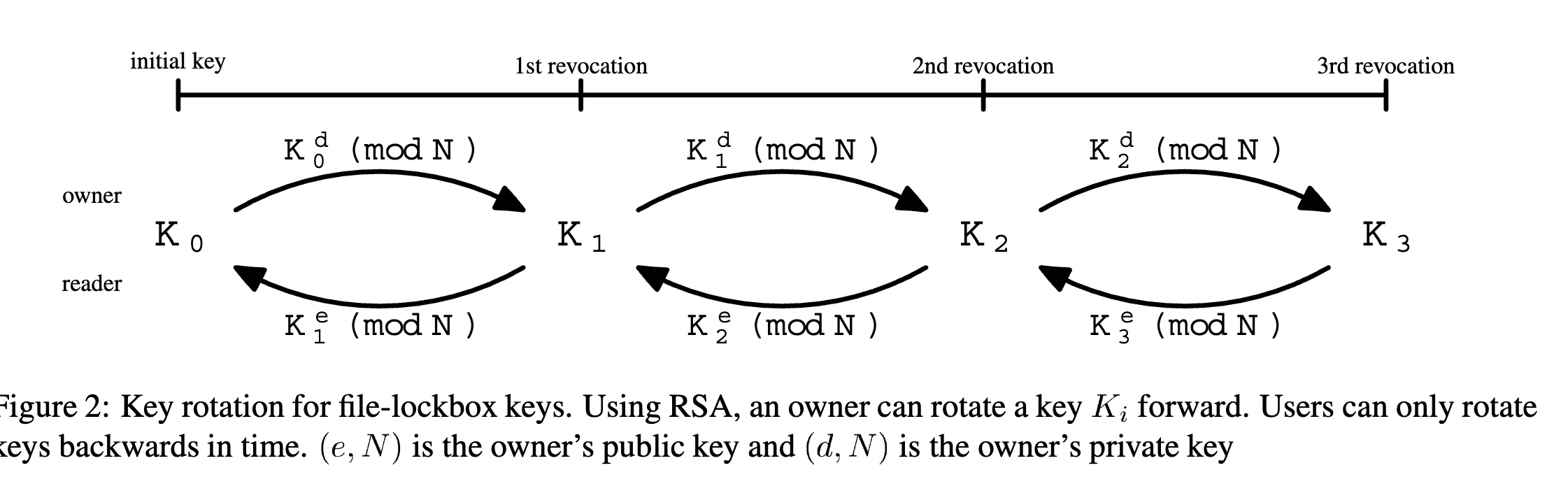
Plutus: Scalable, secure file sharing on untrusted storage
论文里实验才几KB每秒。泪觉时代已经过了20年了。这种鉴权系统对现在来说软件的开销已经够大了。
Lethe: Secure Deletion by Addition
Designed secured copy-on-write over ZFS using the keyed hash forest.

